Important Strings
Basic static analysis of the malware sample can be used to discover more about the malware, for example, look for important strings such as:
- URL's, including C&C's
- PowerShell and command prompt commands
- Configurations for the malware
- Registry entries - possibly for disabling services or maintaining persistence
- API's - useful for describing the malwares functionality
- PDB (created during the visual studio compilation process) strings - can help in identifying the malware by name, and connecting it with other variants or families of malware
- Formatted (printf in C++) strings
- Mutexes
- Processes to inject into, AV processes (detection and termination thereof)
- File paths that reveal funcionalities
- Passwords and encryption keys
- Public keys (for PKA encryption)
PE (portable executable) Header
The PE Header, or "executable files header", is an important place to begin when you start with basic static analysis of a malware sample. There are various open source and free tools available for this task, as well as paid versions, for this demonstration, I will be using the free version of PEStudio. The executable file is organized into a specific structure, the PE header contains useful information, for example, the PE Header sets the stage for the running process by including for example import and export tables detailing the API's and DLL's necessary for the program to run.
- PE header separates the code and data into sections
- Each section has separate permissions.
- The file is expandable in memory
- Supports dynamic linking
- Supports relocation
- Portable for any subsystem, processor, and type of file.
A Note On Unpacking the Malware Sample
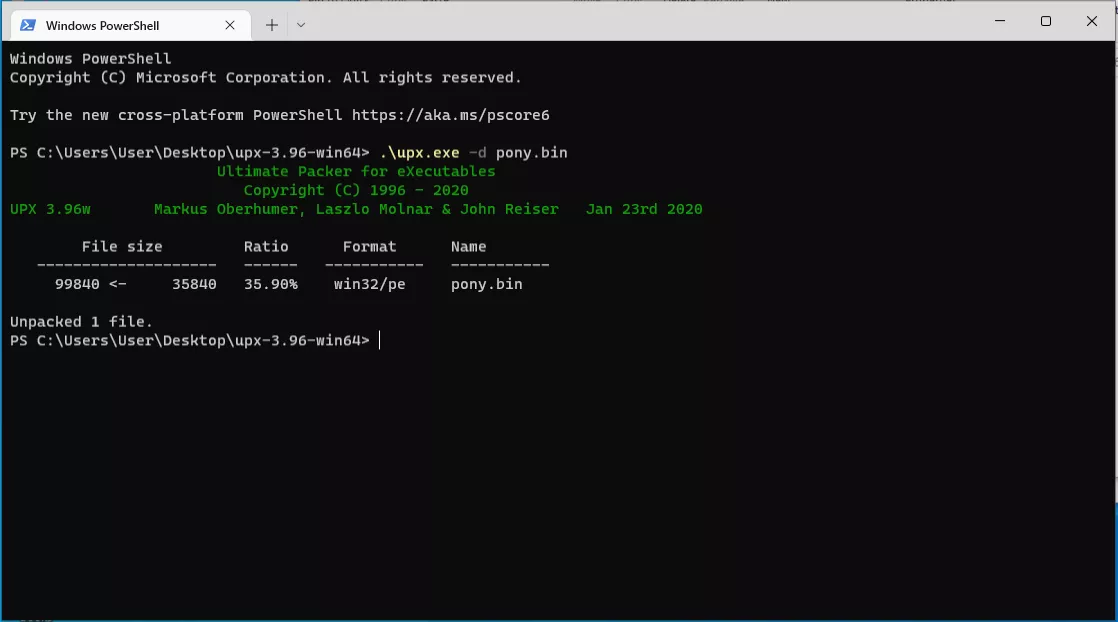
Here I will use UPX to unpack the malware sample before loading it into PEStudio for basic static analysis. Take note of the sections columns, which are not available before the sample has been unpacked, but become available immediately after unpacking. I will be using a sample of Pony AKA Fariet malware: Pony Malware Any.Runs.
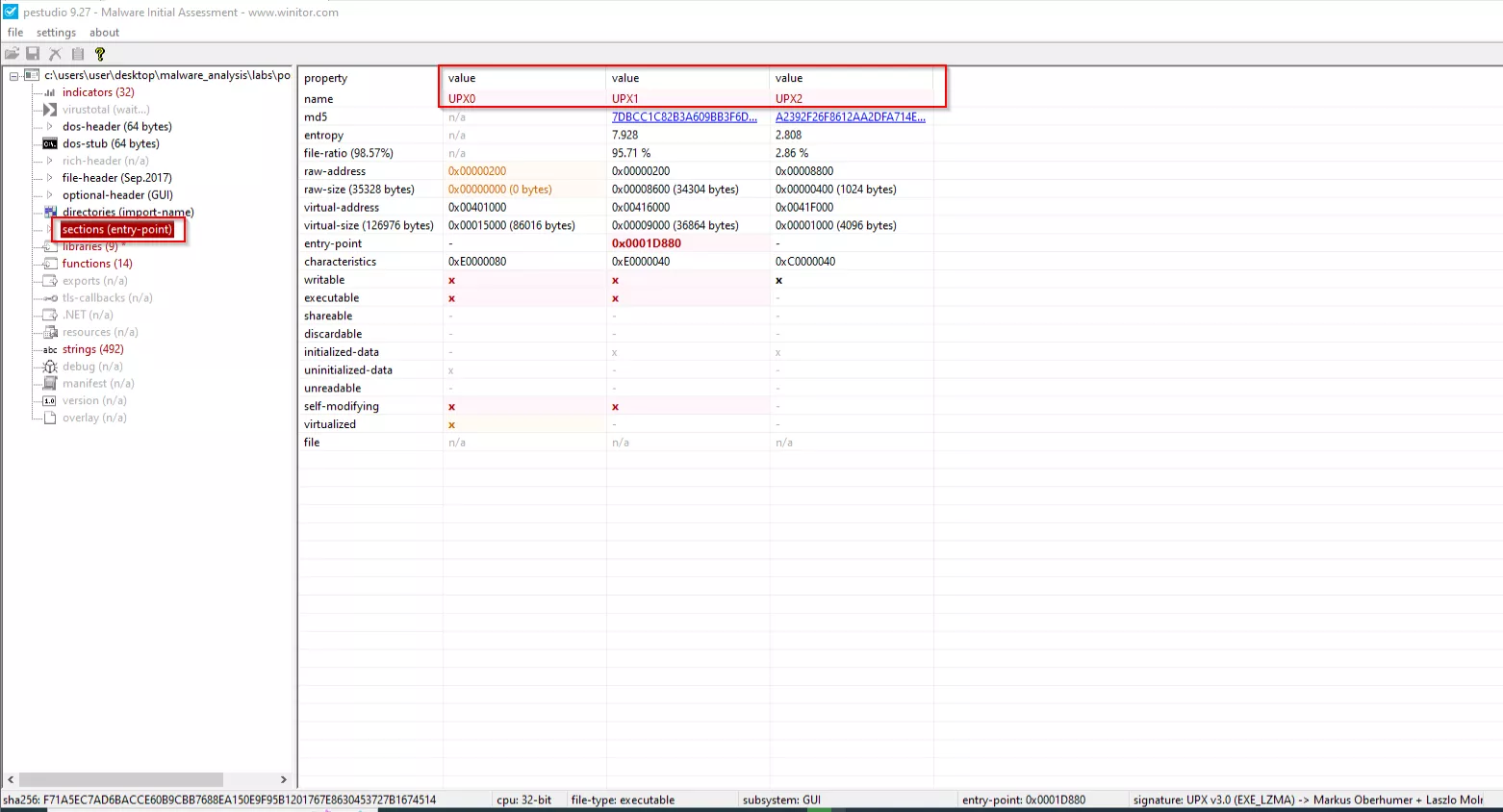
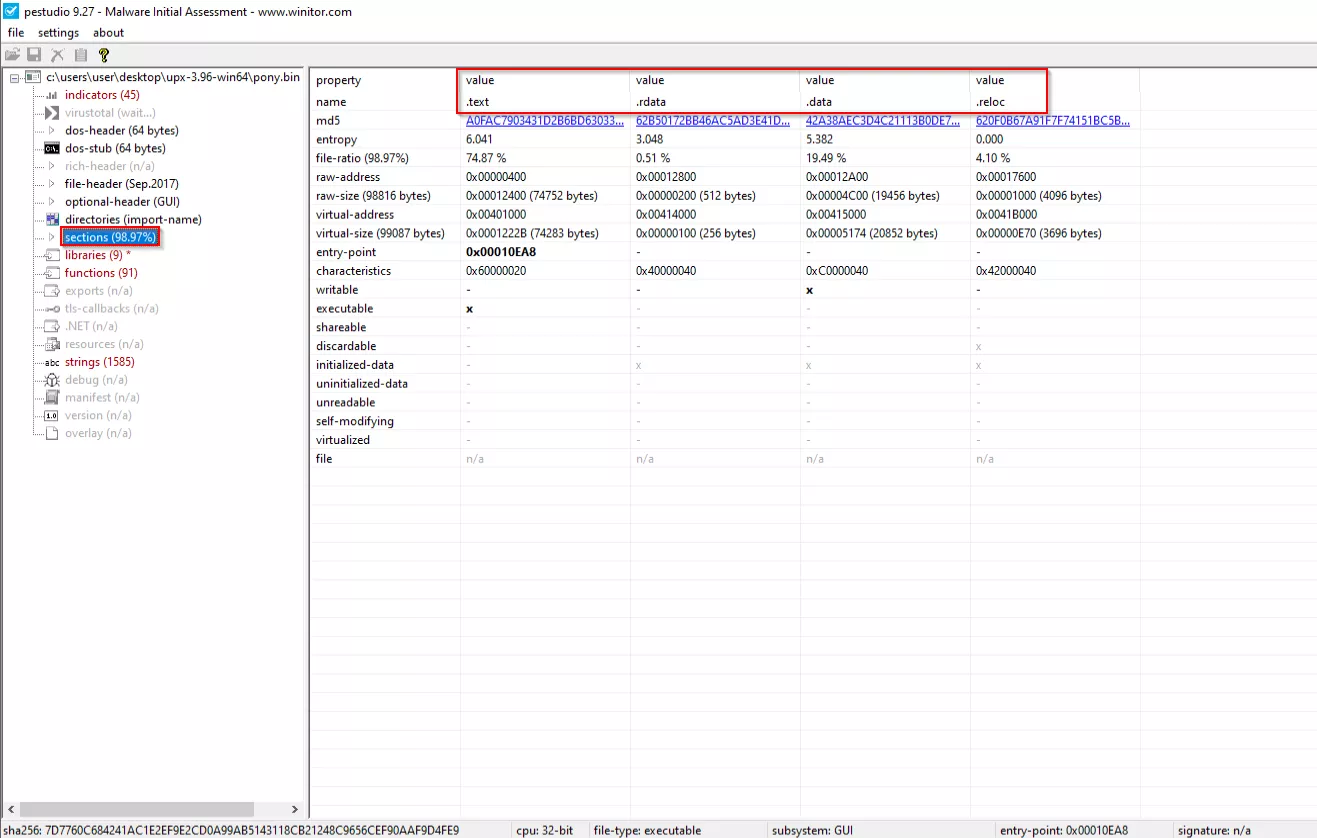
Searching for Strings in PE Studio
After opening the unpacked sample in PEStudio, I select the strings section from the left hand pane, and go through the section of strings looking for interesting and important strings, the first thing that I notice is a GUID, that looks like a Windows unique identifier, I copy this string and search in Google, which immediately returns a result for Pony AKA Fariet malware:
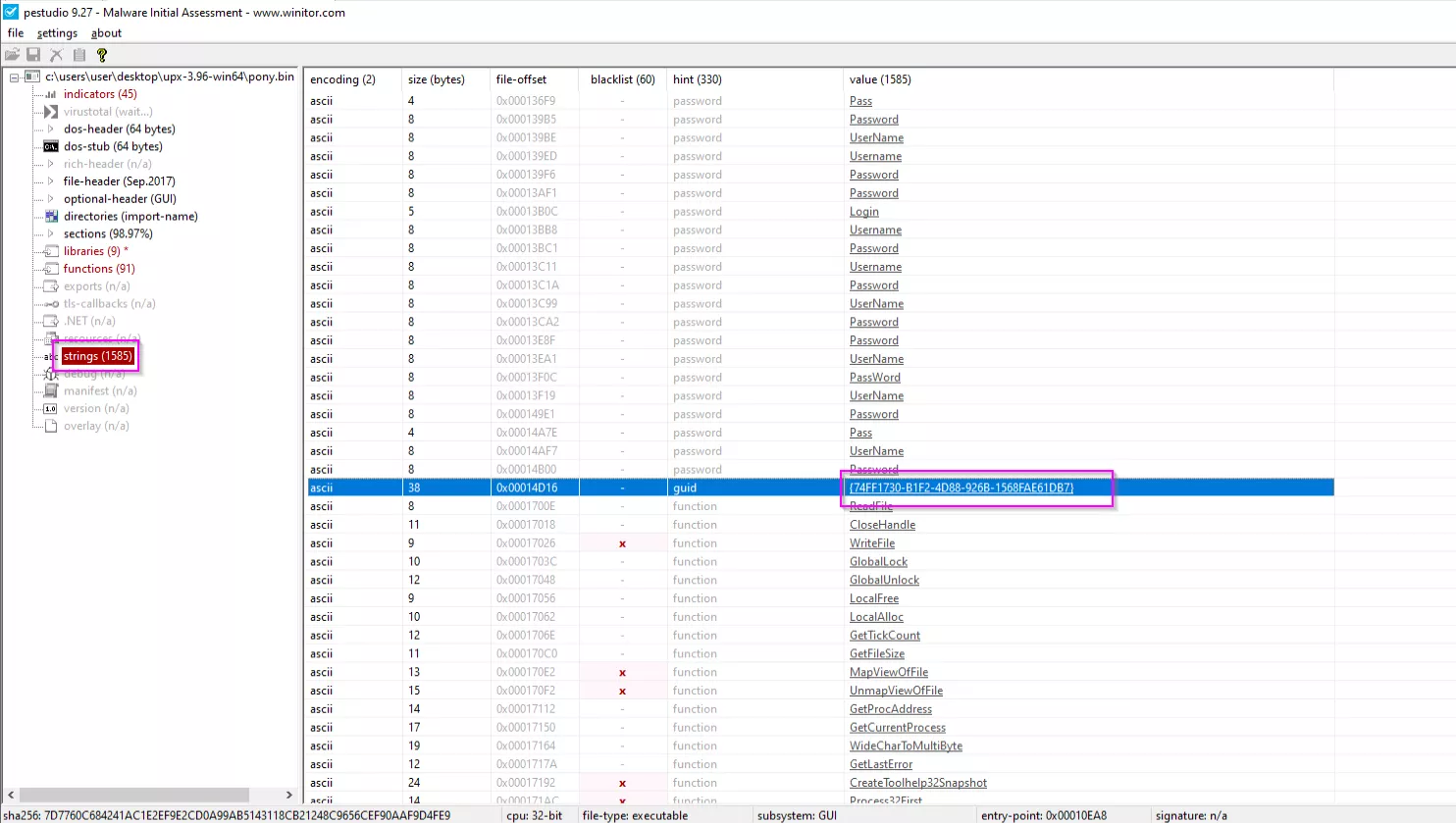
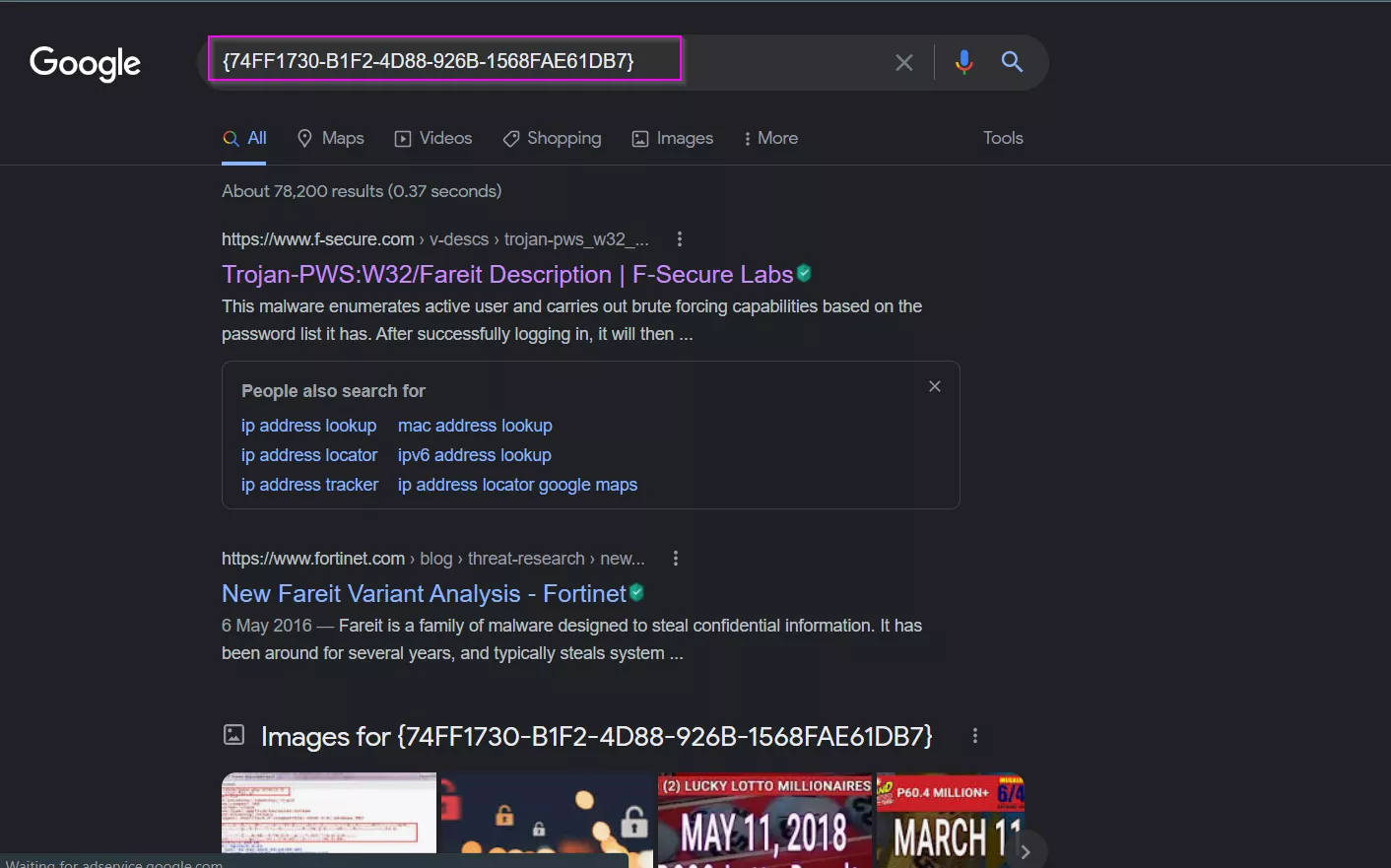
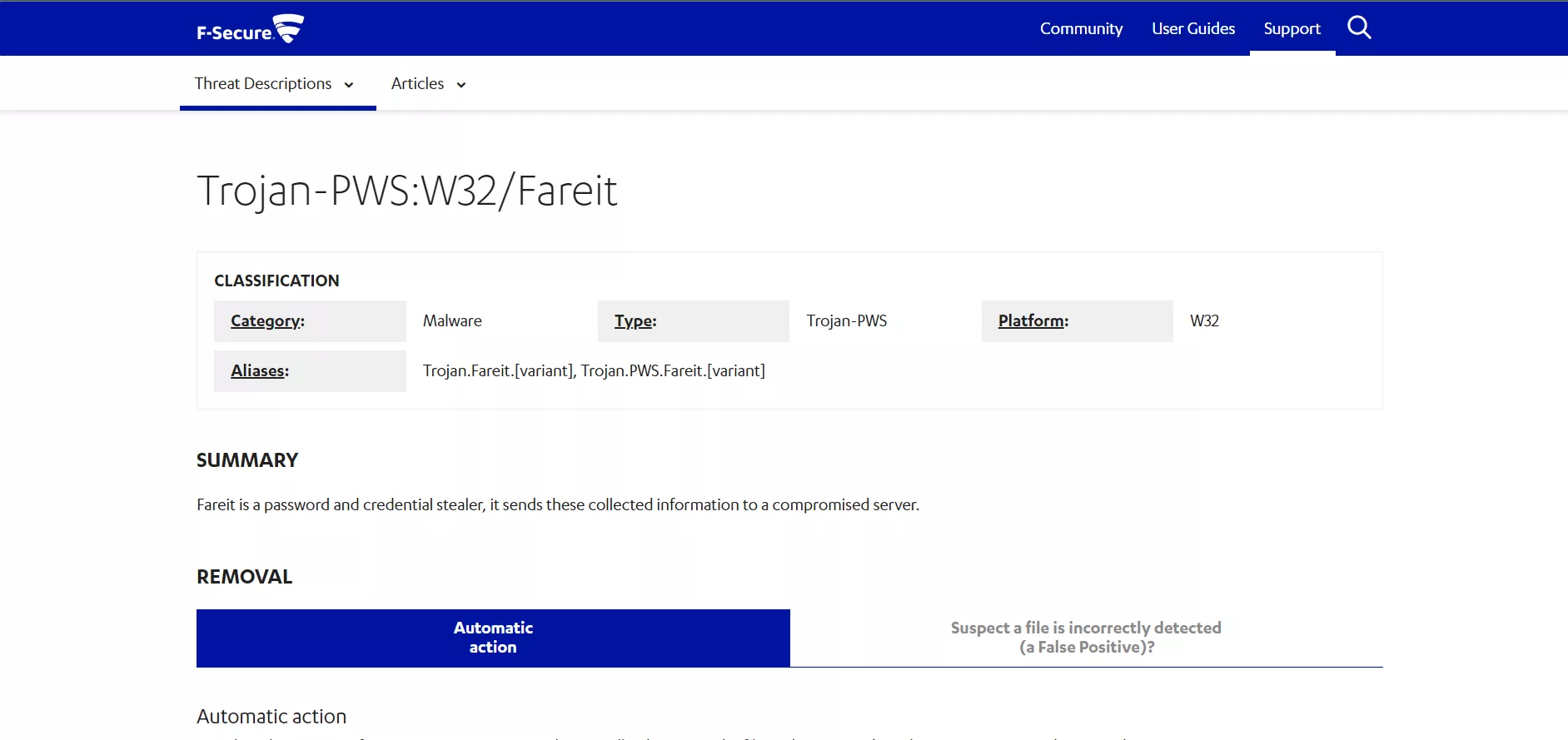
I continue to search in the strings, and I notice a URL that I investigate in Google, and I am returned the (now removed from the web) C&C server of the malware:
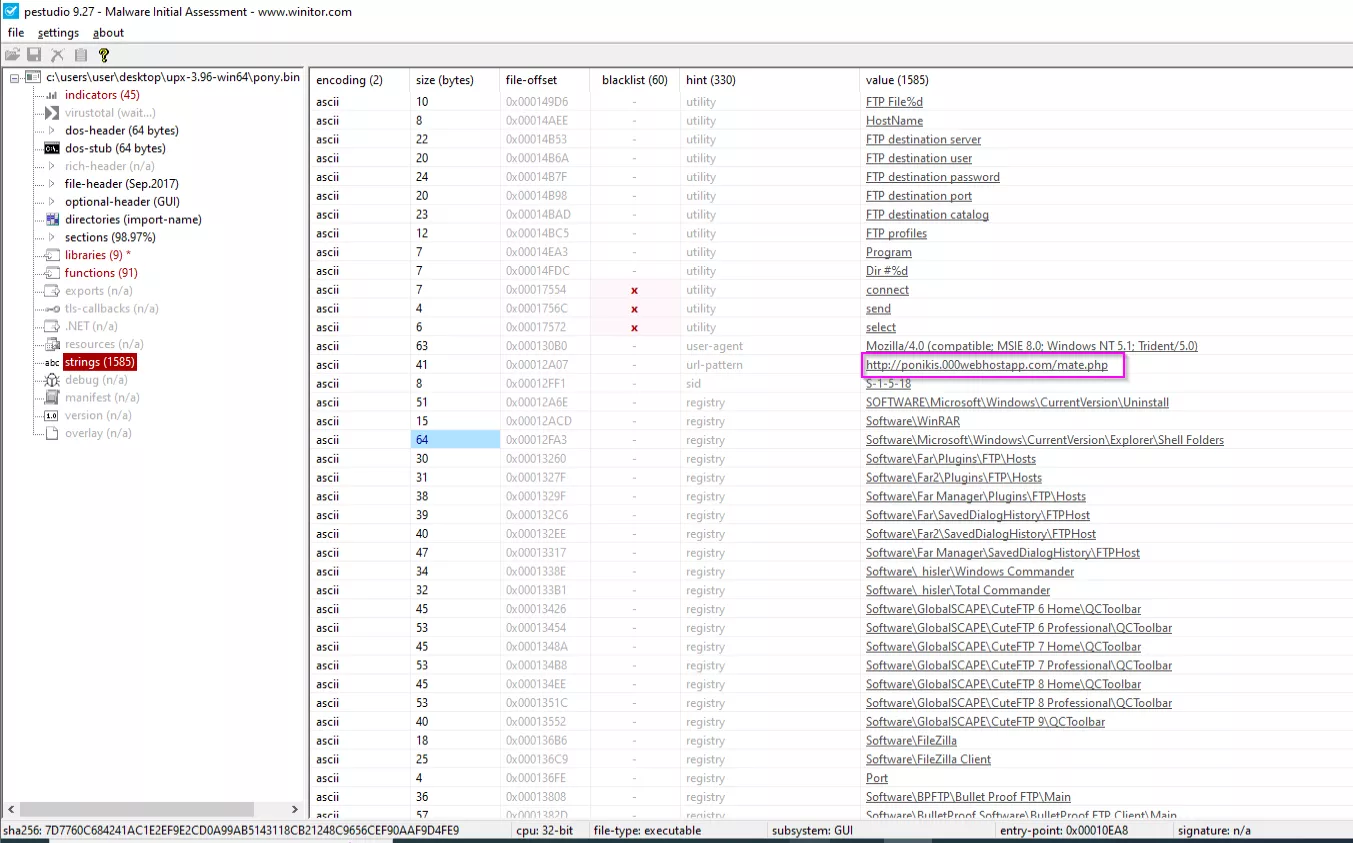
Share with your network
Grant Knoetze
IT Support Specialist Cybersecurity Analyst Software Developer