Use PowerShell to Remote Into a Machine for Investigation as an
Alternative to RDP,
to Protect from
the Threat of Credential Theft by the Attacker when Remoting Into a Machine for
Investigation
Incident Response Process:
- Preparation
- Detection and analysis
- Containment, eradication, recovery
- Post incident activity, including reporting and communication
with stakeholders
Incident response process courtesy of NIST (US National Institute for
Standards and Technology):
NIST computer security incident handling guide
Why PowerShell?
- Gives ability to dive deep into the system.
- PowerShell gives the ability to automate this process
across scale.
- PowerShell is a secure remoting protocol
Enable PowerShell Remoting
Follow the steps illustrated in the series of snapshots
below to enable PowerShell remoting on your home network or any other network
or machine that is not part of a
domain or Active Directory...
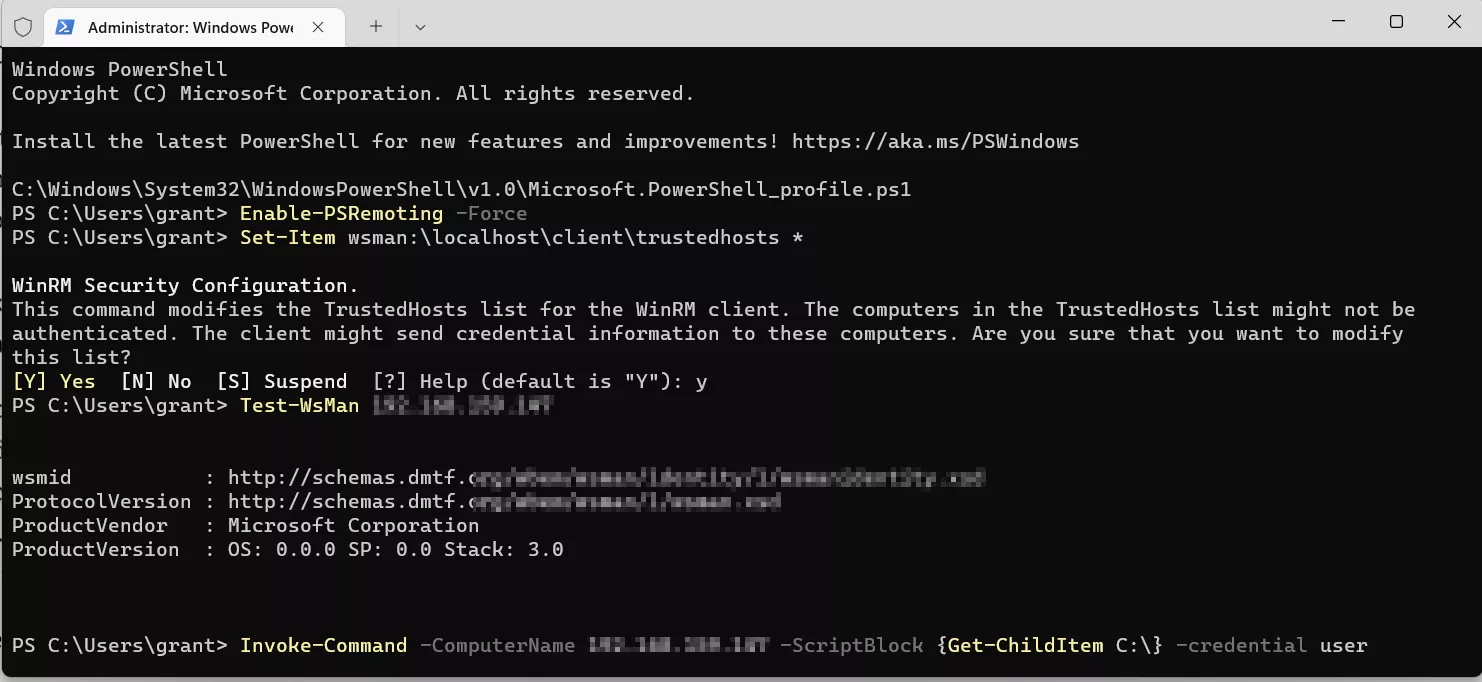
First, enable PSRemoting and set trusted hosts to all
by using the wildcard character (*), you can also set trusted hosts
by IP address or computer name.
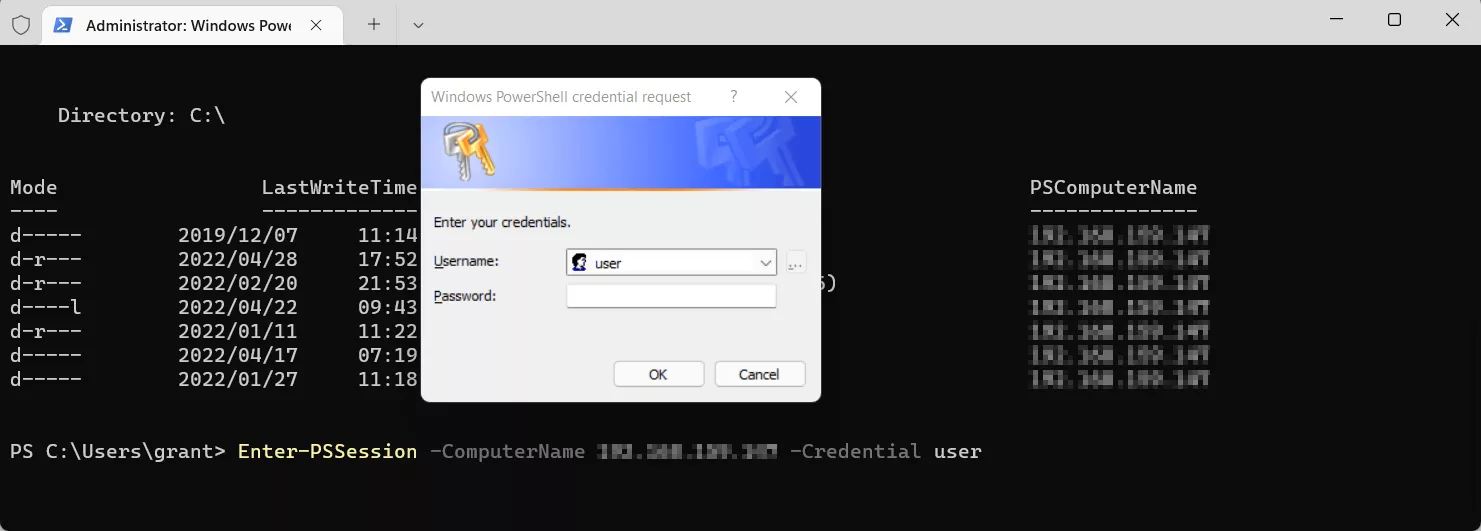
Next, enter the PSSession using the Enter-PSSession cmdlet as seen below,
use the target machines IP address or host name, and the user account you wish to access.
The message box that appears will have the user account that was just supplied, enter
the password or pin of that user account.
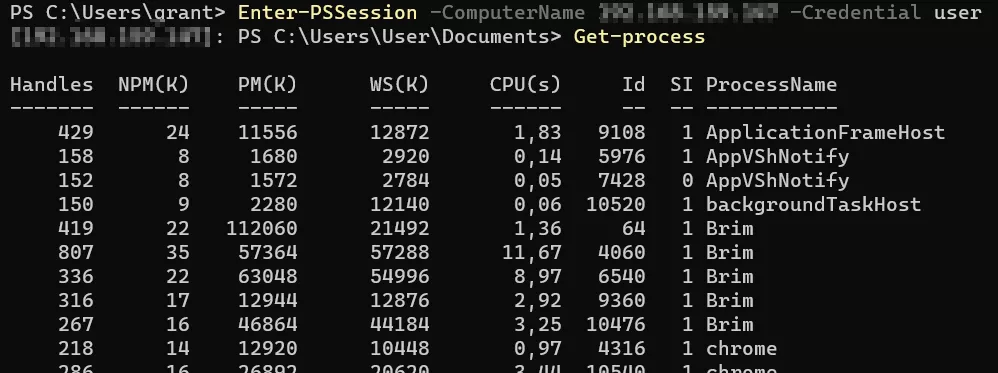
You can now run PowerShell commands in the remote machine, and
begin the PowerShell hunting process.
PowerShell remoting uses port 5985 for http and 5986 for https, and should
be
used to look into...
- Process list and loaded DLL’s….
- Running services
- Scheduled tasks
- Network connections…
- Non-volatile data(reg,mft etc)
- Windows event logs(.evtx files)
- Installed apps
The following code is an example of a script that can be run in a remote
session to
get the parent process of a running process using a WMI object.
What to hunt for?