Use Sysmon to Detect Malicous Documents Used in Targeted Spearphishing Attacks
Incident Response Process:
- Preparation
- Detection and analysis
- Containment, eradication, recovery
- Post incident activity, including reporting and communication with stakeholders
Incident response process courtesy of NIST (US National Institute for Standards and Technology):
NIST computer security incident handling guideWhy Sysmon?
"System Monitor (Sysmon) is a Windows system service and device driver that, once installed on a system, remains resident across system reboots to monitor and log system activity to the Windows event log. It provides detailed information about process creations, network connections, and changes to file creation time. By collecting the events it generates using Windows Event Collection or SIEM agents and subsequently analyzing them, you can identify malicious or anomalous activity and understand how intruders and malware operate on your network." - Courtesy: Microsoft Documentation for Sysmon
Microsoft Documentation for SysmonThe Scenario: An Attacker Has Used a Malicous Document in a Targeted Spearphishing Attack to Gain Initial Access Into the Organization
In this scenario, the attacker has utilized a malicious document as part of a targeted spearphishing attack to gain initial access into the organization. The intended victim has recieved a phishing email, and opened a malicious document, enabled editing(macros), and become infected in the first stage of a targeted malware attack. The attacker is an APT group, all malware and command and control servers are custom designed and written to bypass AV and EDR.
Sysmon Configuration
Sysmon takes configuration files in the form of XML files, an example of a sysmon configuration file can be seen below:
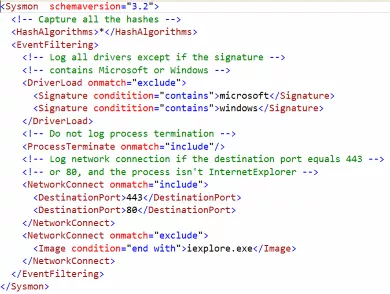
There are various open source projects available on GitHub for Sysmon configuration, I am using the SwiftOnSecurity open source project which is available here:
SwiftOnSecurity GitHubConfiguring Sysmon on my local machine using an XML file from an open source project I found on GitHub:
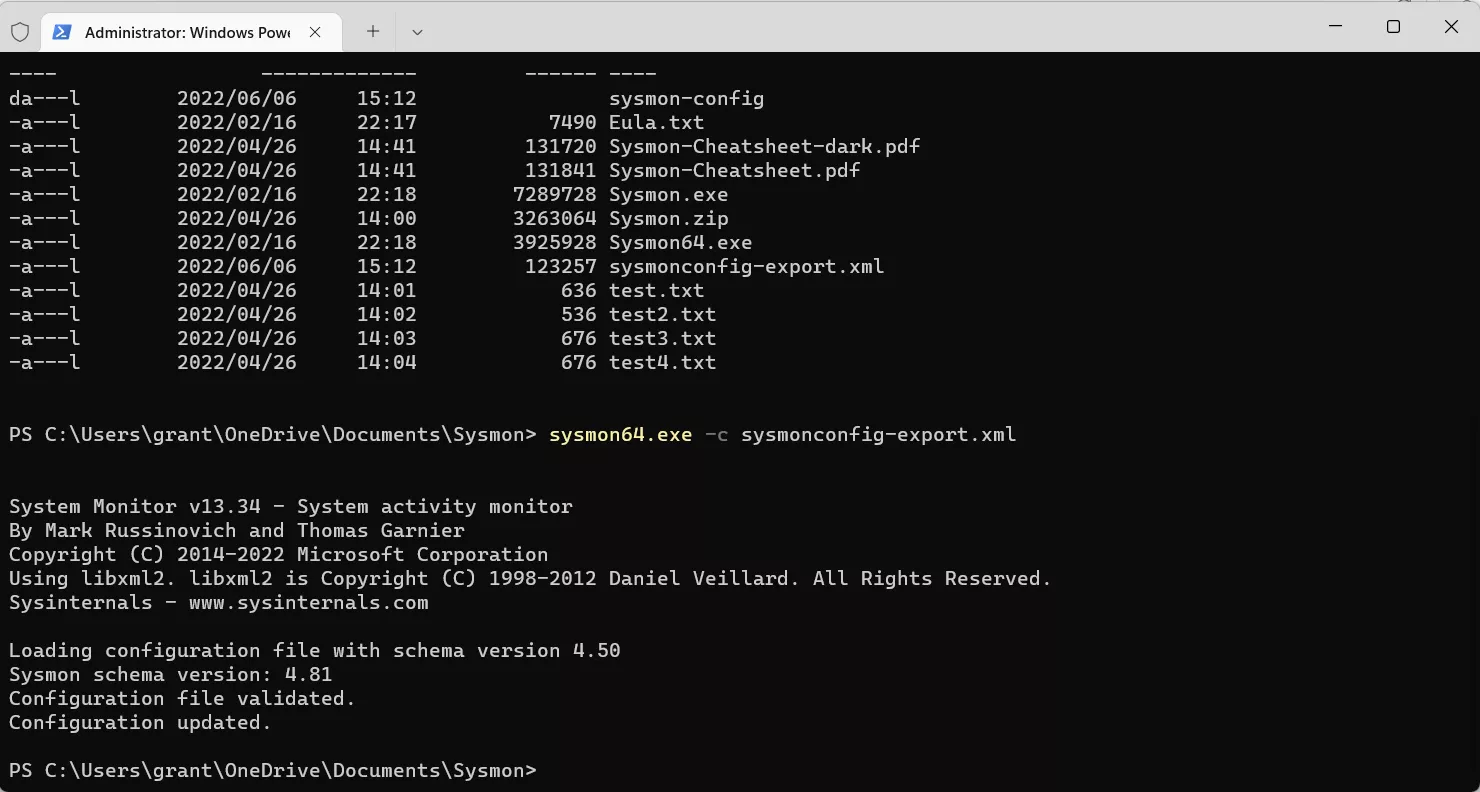
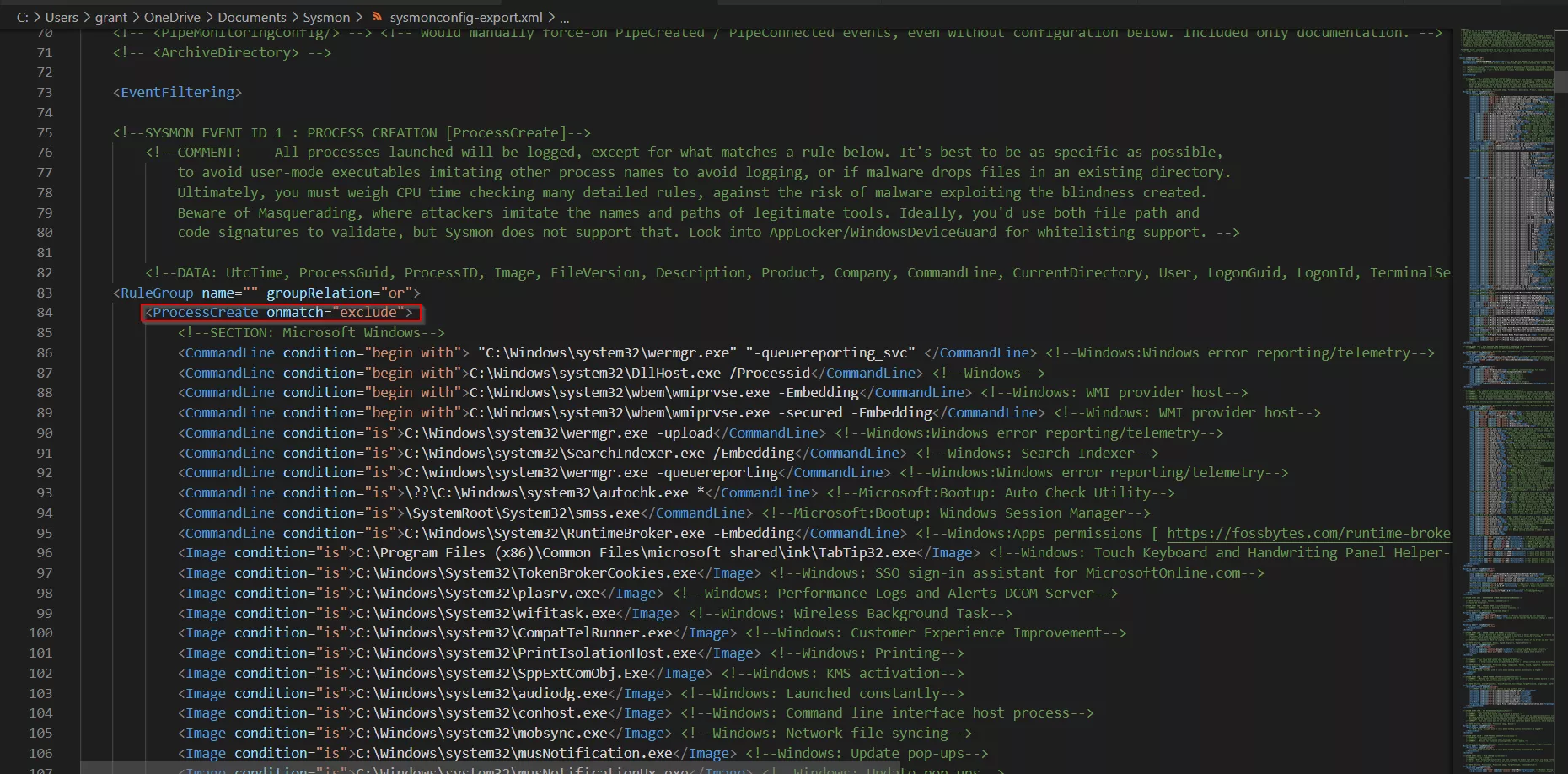
Sysmon XML configuration files can be modified to include or exclude events as per your organization or personal needs, for example, you may want to exclude some Windows process creation events, as seen in the SwiftOnSecurity XML schema below:
The Sysmon configuration XML file can be modified to include a MITTRE ATT&CK technique, as seen below with the inclusion of T1099 in the inclusions:
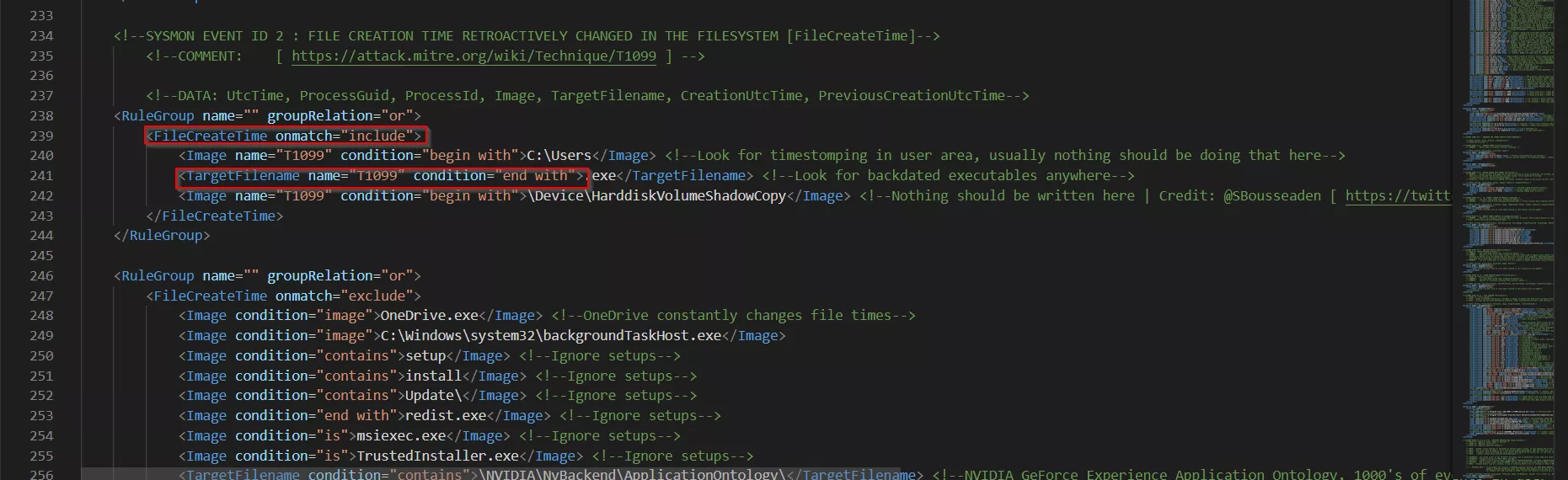
Although this technique has been deprecated, as seen below, hightlighting the importance of staying up to date and relevant:
Investigate Sysmon Logs to Find Attacker Malicious and Executable IP
What is an EVTX file?
The Windows XML EventLog (EVTX) format is used by Microsoft Windows, as of Windows
Vista, to store system log information.
The EVTX format supersedes the Windows EventLog (EVT) format as used in Windows XP.
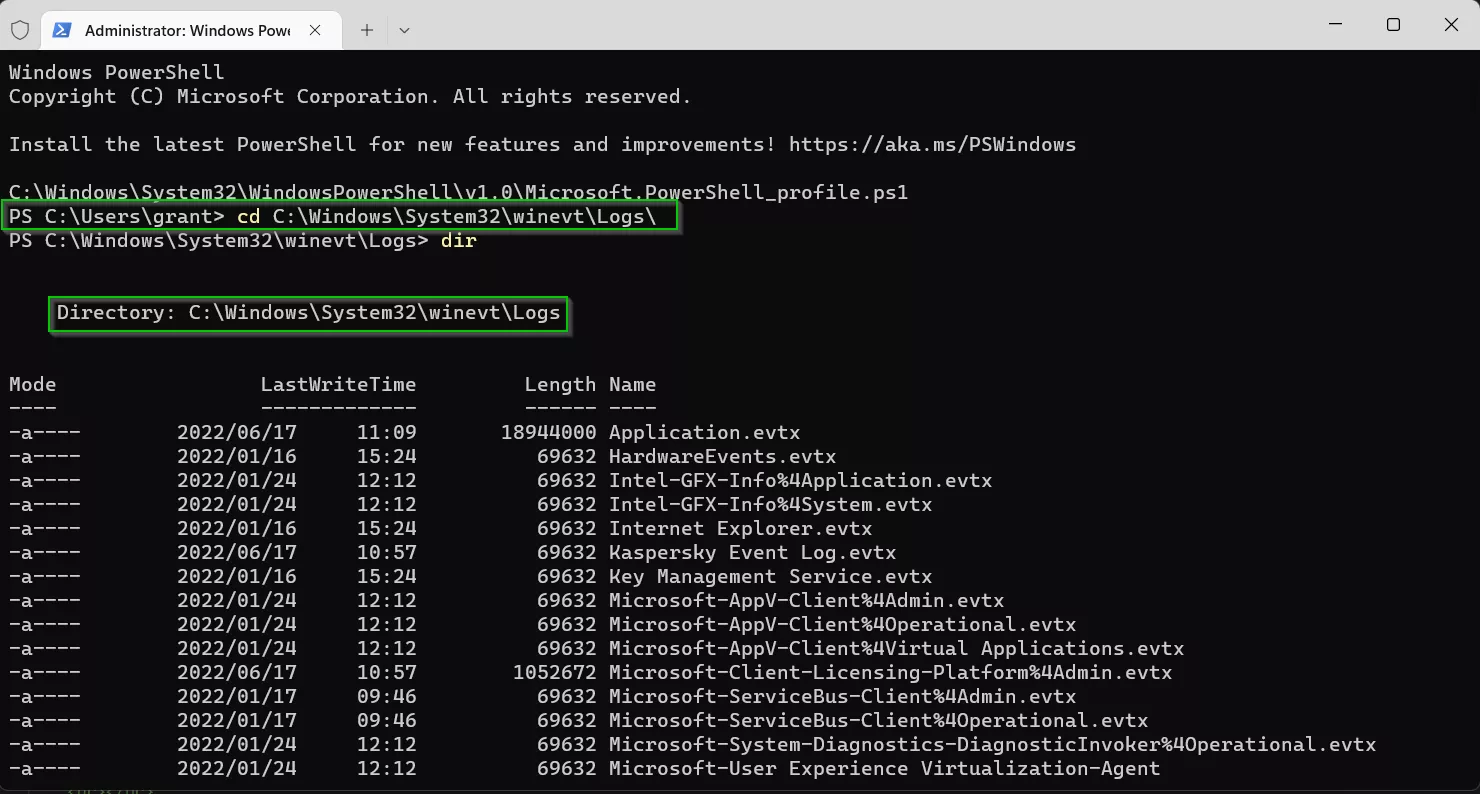
Event log files can be found using the command line at
C:\Windows\System32\winevt\Logs\, as
seen in the screenshot below:
Or, follow these steps to use Event Viewer to save either application, system, or security event log as an .evtx file:
- Open the Start menu and search for “event viewer.”
- Click Settings. On the left, click Event Viewer.
- When the Event Viewer opens, expand Applications and Services Logs.
- Expand Windows Logs.
- Right-click Application and select Save Events As.
- Save the log in the EVTX format.
- Right-click System and select Save Events As.
- Save the log in the EVTX format.
Once Sysmon is running on the machine, and has been configured according to the needs of the individual or organization, use the following steps to locate and save the Sysmon logs in a .evtx format. We will then upload the Sysmon Logs into Splunk to analyse and search for strings which may be telling to malicious activity.
- Open the Start menu and search for “event viewer.”
- Click Settings. On the left, click Event Viewer.
- When the Event Viewer opens, expand Applications and Services Logs.
- Expand Microsoft Logs.
- Expand Windows logs.
- Expand Sysmon logs.
- Right-click System and select Save Events As.
- Save the log in the EVTX format.
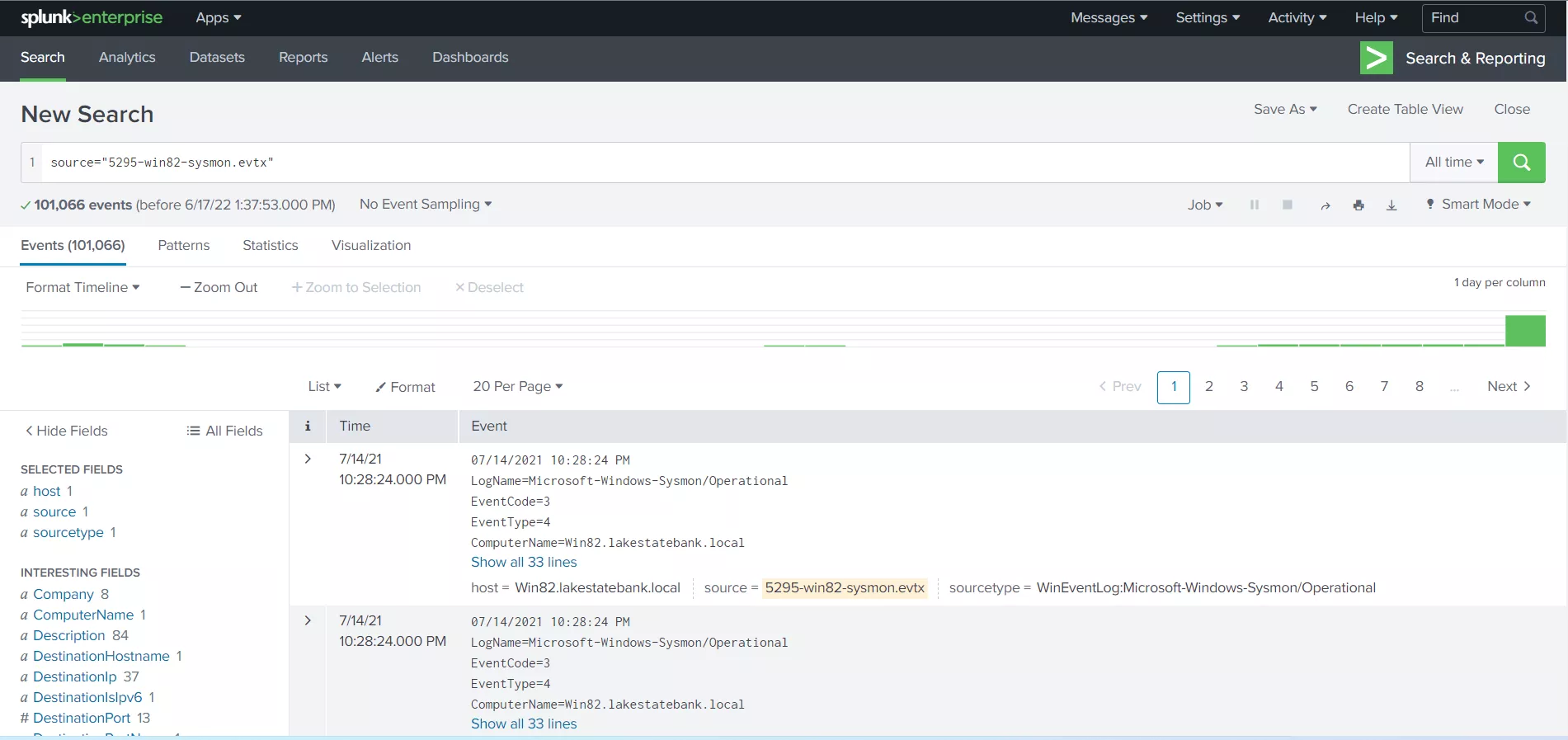
Now we will be using Splunk enterprise to invesigate a Windows event log (.evtx) file to find malicious IP addresses (which may indicate an attacker C2). First, uplod the .evtx file into Splunk, as shown in the following screenshots:
Searching in Splunk.
Once the log file is uploaded into Splunk and searching commences, Splunk will
automatically
identify and parse the information and identify the host, source, and source type, as
seen in
the screenshot below:
Lets return to our scenario for a moment; we said that an
attacker has gained access to the organization by delivery of a malicious office
document
as part of a phishing attack, the victim opened the document, enabled editing, and
in this way
allowed a malicious script to run as the first step in gaining entry into the
organization. Thus, we are
looking for the following possible Sysmon events (looking at Winword as the parent
process in this case
since a malicious word document was used).
The scenario detailed above is an example of a hypothesis that may be formed as
part of the threat hunting process in the organization, in other words, as a threat
hunter or
part of a threat hunting team, we have formulated the hypothesis that the organization
has been
breached, and the attacker/s have used a malicious microsoft word document with a
phishing email.
Now we are searching for specific indicators of such an attack, using Sysmon logs and
splunk
to search through an event log to find these events.
- Process creation (Event ID: 1).
- File creation (Event ID: 11).
- Network connection - as the script may connect to an IP to drop a successive stage in the malware event, or connect to a C & C directly (Event ID: 3).
The event and event ID in Splunk search are highlighted in the screenshot below:

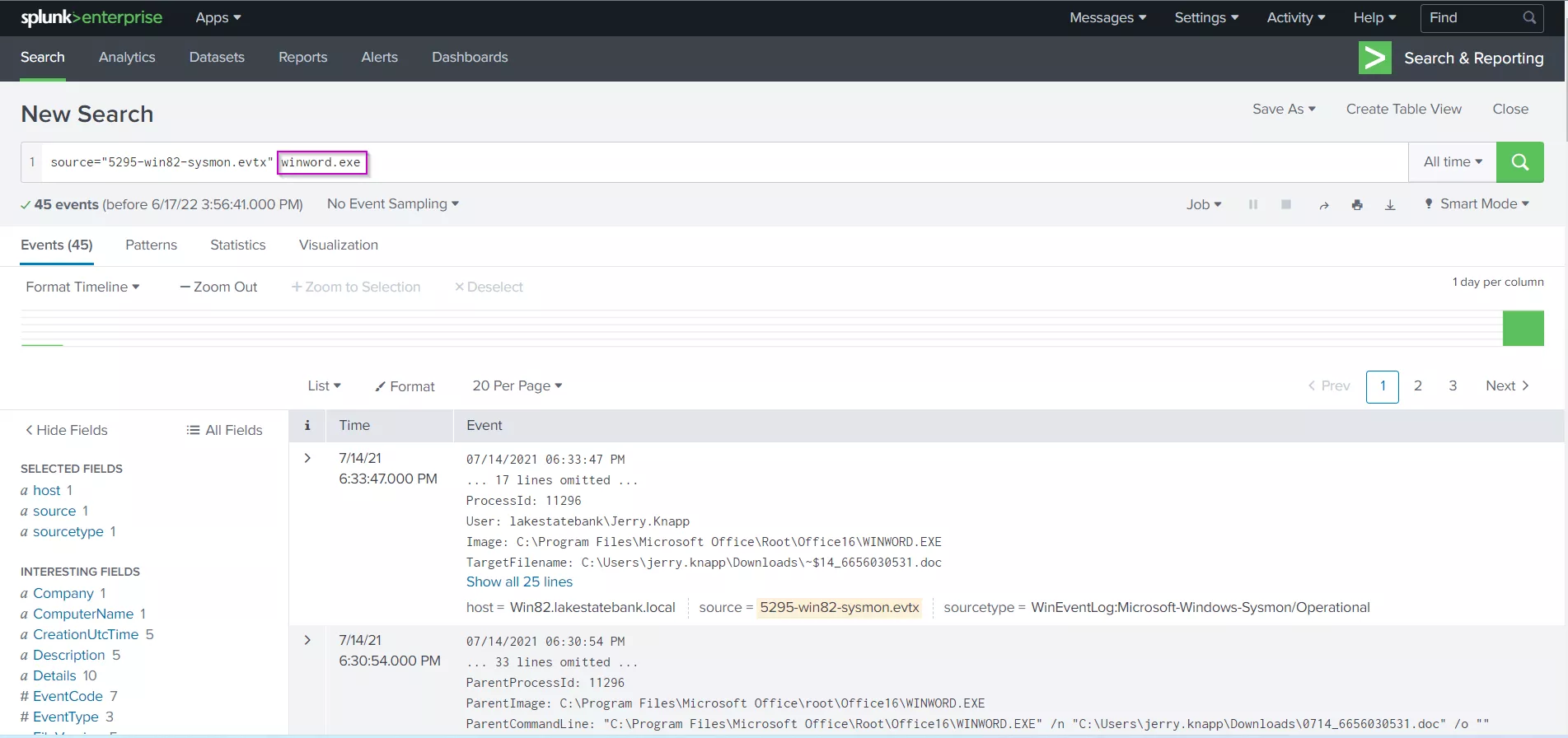
As mentioned above, we are searching for Winword.exe as a parent process according to our hypothesis, so lets enter "Winword.exe" into the search bar and search for it in the logs.
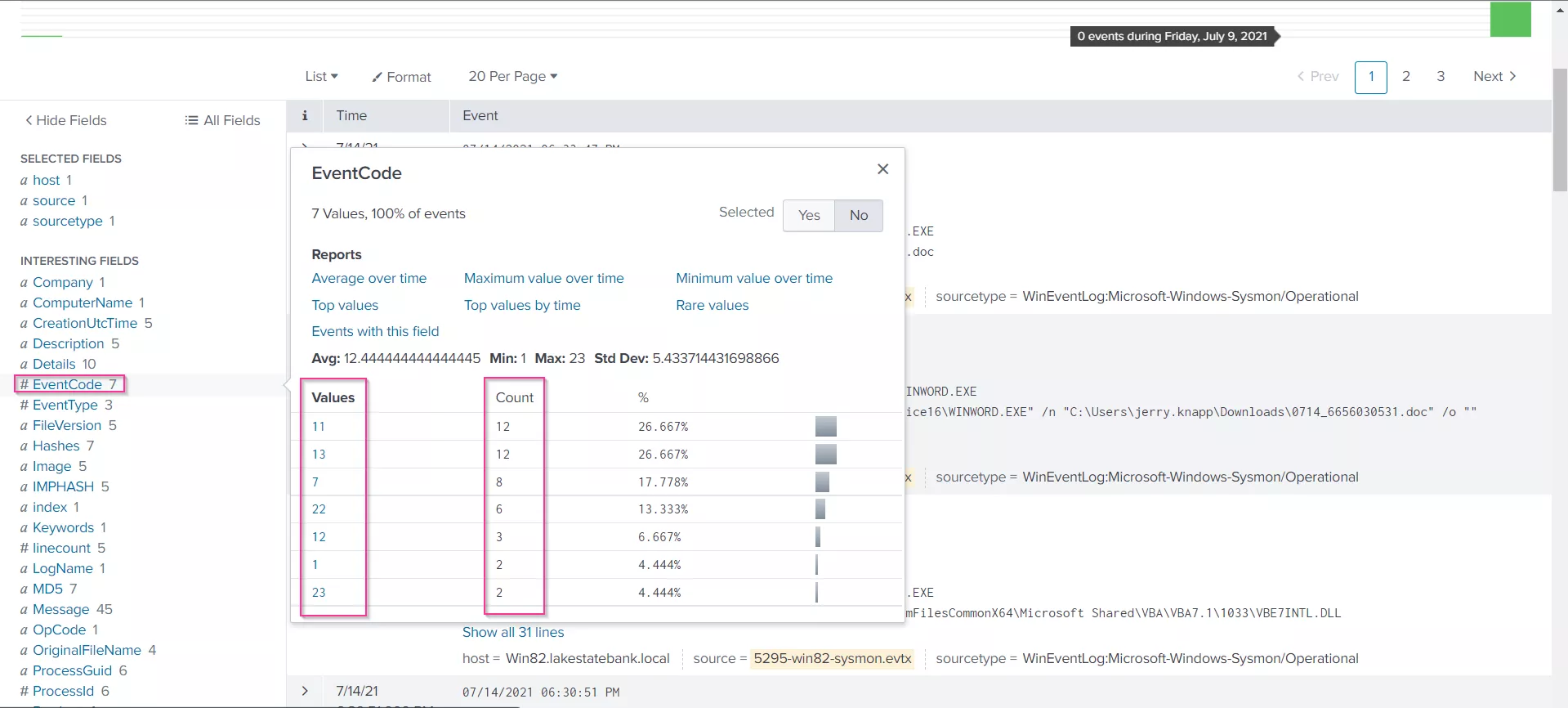
Scroll down to the "Interesting Fields" section on the left hand pane of the Splunk Enterprise New Search page, for our purposes, the "Event Code" button wil be useful. Click on it, and a box appears tabulating the Sysmon event codes appearing in the logs, along with thier frequencies, and some other statistics.
Since we are interested in Event ID: 1, which is representative of a new process being created, lets click on it. We are then presented with the two events with the Event ID: 1
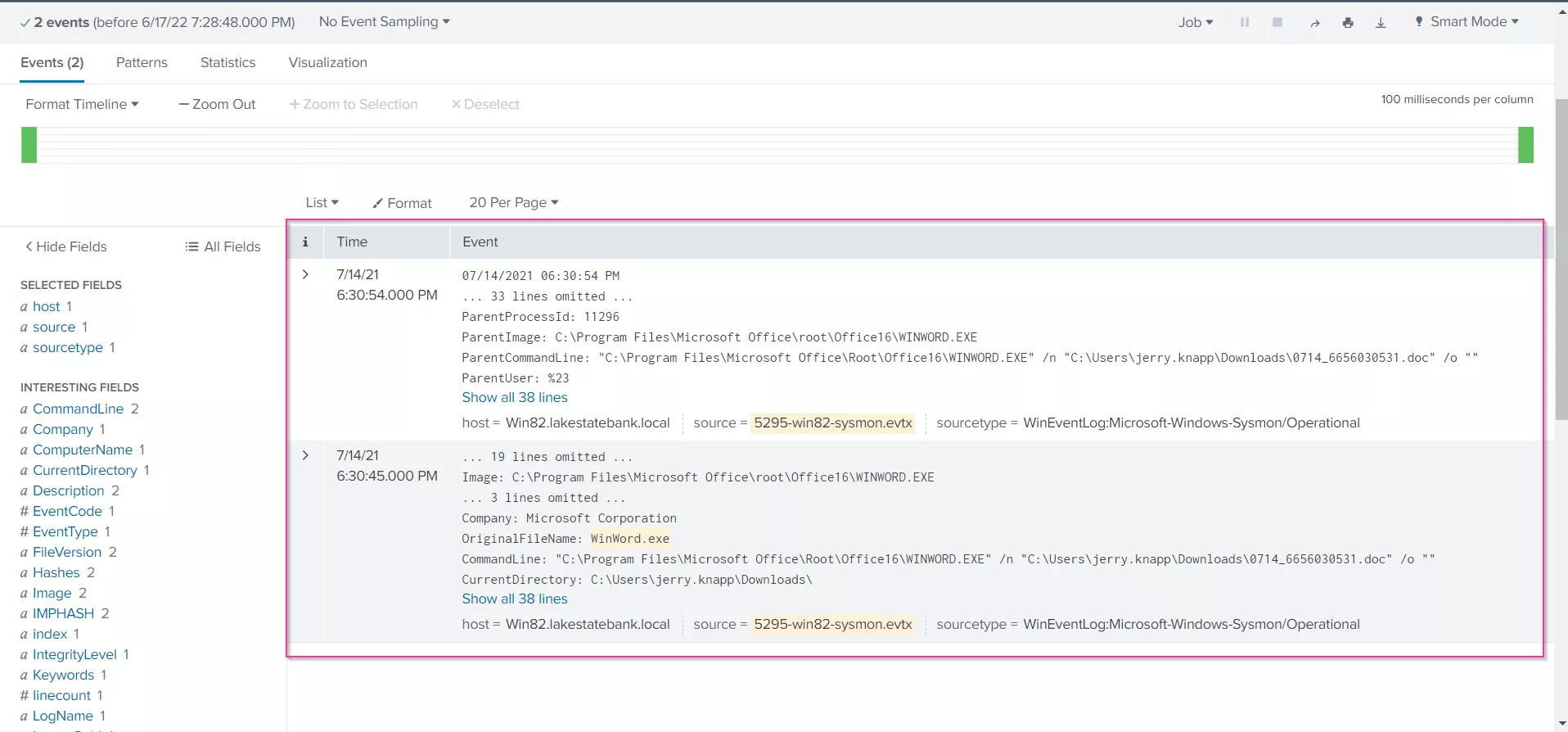
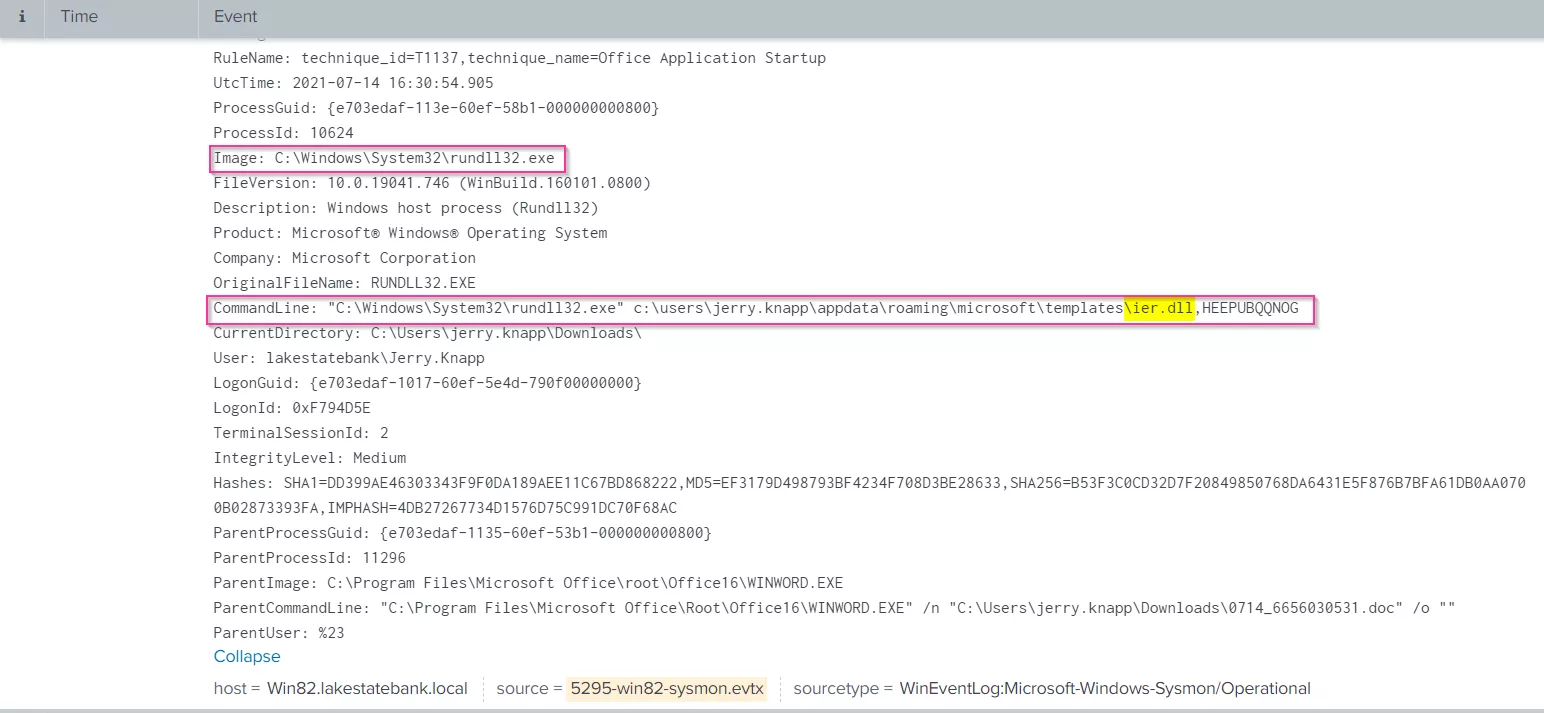
If we expand the first event, we see that Winword.exe has executed rundll32, along with the exact command line, having dropped a file called "ier.dll", in other words, using a signed Windows application to download and run a malicious dll file, as we can see, in the user Downloads folder.
Keep following me on social media to stay tuned for the follow up to this post...
Share this with your network
Grant Knoetze
IT Support Specialist Cybersecurity Analyst Software Developer