When to Perform Memory Forensics
The decision to make a memory dump (aquisition), is taken when there has been an incident. There must be some suspicion that the machine has been compromised. Memory dumps and memory forensics can be very helpful in the incident response process. First, get a memory dump (memory aquisition), using a tool such as dumpit.
Volatility3
Volatility3 is an open source tool that we will use for memory forensics.
Investigating Processes
One of the first things that we will do is investigate the running processes. Volatile info including the process list etc. To get the running processes run the PsList command to do so.
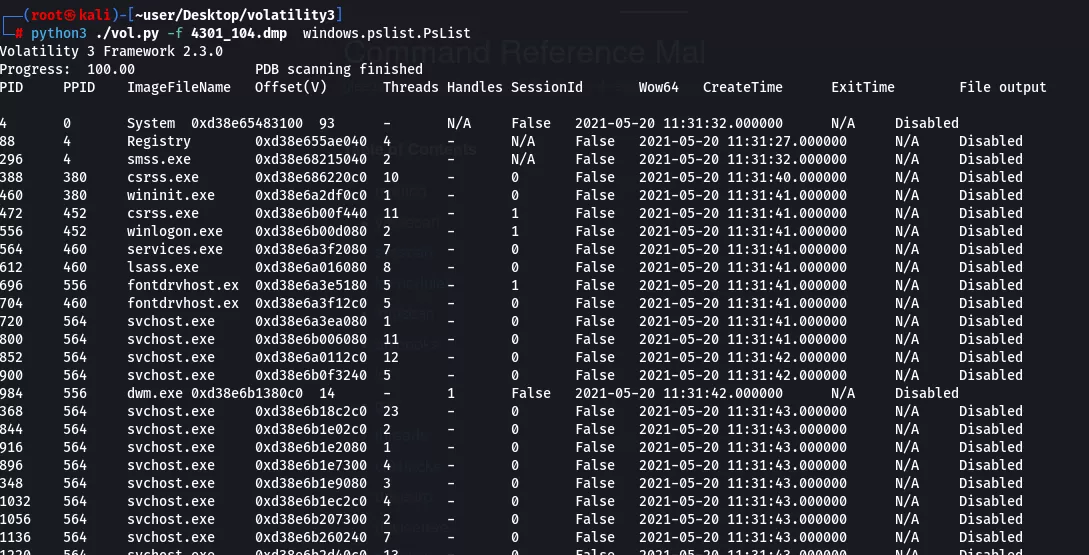
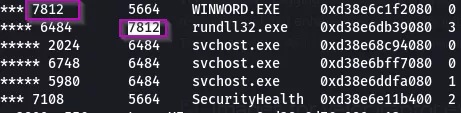
The Pstree command will be helpful in finding suspicious processes launching other processes. As we can see in the snap below, WINWORD.EXE is launching rundll32.exe which we can assume is registering a DLL, in this case a malicious one (IER.dll from the same incident referred to in my previous post)
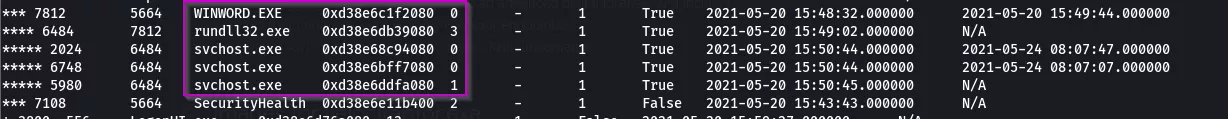
Notice that rundll32.exe's parent process ID (PPID) is the same as the process ID (PID) of WINWORD.EXE.
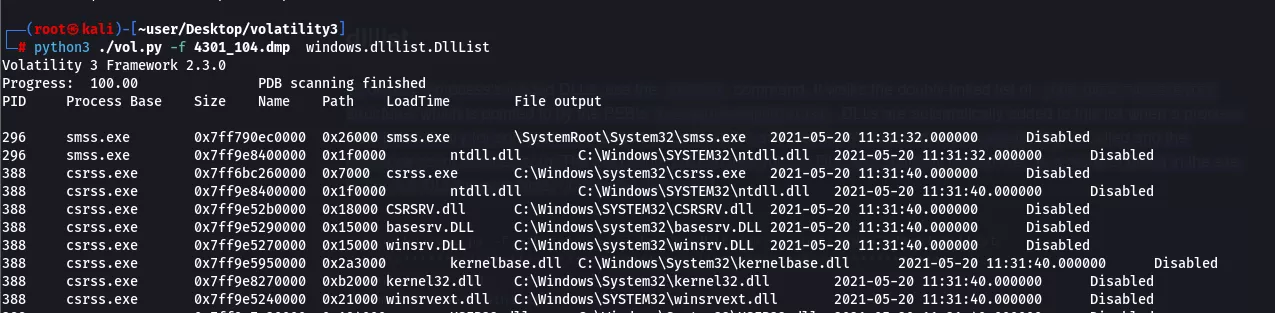
Display loaded DLL's
To display a process's loaded DLLs, use the dlllist command. It walks the doubly-linked list of _LDR_DATA_TABLE_ENTRY structures which is pointed to by the PEB's (process environment block) InLoadOrderModuleList. DLLs are automatically added to this list when a process calls LoadLibrary (or some derivative such as LdrLoadDll) and they aren't removed until FreeLibrary is called and the reference count reaches zero. The load count column tells you if a DLL was statically loaded (i.e. as a result of being in the exe or another DLL's import table) or dynamically loaded I run the dlllist command and output the contents to a txt file, which I then search using grep for the PID of the suspicious process that I have previously gathered, to see which DLL's were loaded by the process. The DLL's can be dumped and you can run the strings.Strings command to search for important strings.
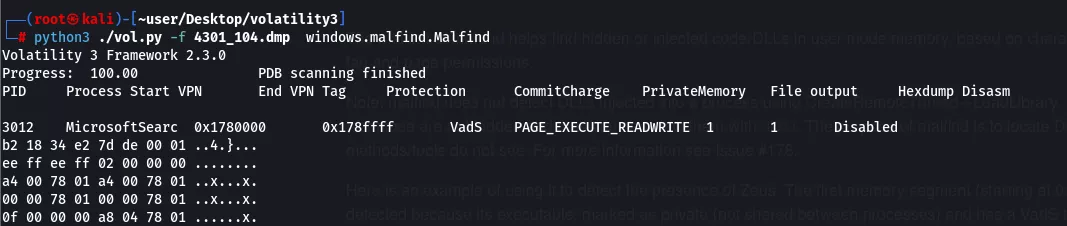
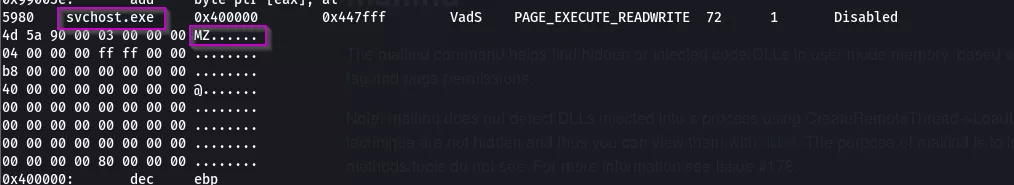
Using Malfind
The malfind command helps find hidden or injected code/DLLs in user mode memory, based on descriptions such as virtual address descriptor (VAD) tags and page permissions. The purpose of malfind is to find DLL's that standard methods and tools do not see. Malfind will look for PAGE_EXECUTE_READWRITE in private memory.
Share with your network
Grant Knoetze
IT Support Specialist Cybersecurity Analyst Software Developer