Defense Evasion forms part of strategically hiding or obfuscating important information, for example: strings.
- Advanced - Targeted, coordinated, purposeful
- Persistent - Month after month, year after year
- Threat - Attacker with intent, opportunity, and capability
Cyber-Kill-Chain definition courtesy of: Lockheed Martin.
Lockheed Martin Cyber Kill ChainThere are 3 main tactics employed for defense evasion, namely;
- Hiding from the defenders - Techniques to encrypt and obfuscate data are employed.
- Blending in with the defenders - Disguise the malicious activity as legitimate.
- Attacking the defenses, defense infrastructure.
Using C++ to Encrypt and Decrypt a String (URL or IP address for this exercise)
String encryption can be added into the C++ RedTeamAgent trojan software, as seen in the code below:
File Signature and Heuristics Bypass: Strings Encryption
Strings are important to blue team, malware analysts and
anyone doing any defensive security, and as such are commonly obfuscated
using encryption by the attacking side. For the attacker, this can be
a double edged sword as IDS/IPS and especially machine learning based tools will
immediately flag encrypted strings (especially domains and URL's) as
suspicious.
Strings are a good place for an investigator to begin looking for clues in text.
This step may form part of the basic static analysis of a malware sample.
For the sake of understanding this concept on a deeper level, let us
make an example of using strings to understand more about the malware...
Important Strings
Binary data contains strings which may be important to the SOC analyst or incident responder, and certainly to the malware analyst. The analyst/responder will have to extract meaningful strings from a set of data. As an attacker, we should have an awareness of what our targets defenders will be looking for, and certatinly we want to keep key pieces of information such as IP addresses obfuscated to delay and prevent our detection, and the detection of our activities. A real world APT group will be interested in obfuscation of text and other string data that has to be transmitted over a network.
- Commands for command prompt CLI (cmd.exe etc) although this is suspicious and almost certainly will be flagged by ML tool
- Command and control (C2) servers or other functional URL's
- Registry entries
- printf* strings
- API's
- Processes, mutexes, file paths, passwords, keys, and PowerShell commands
File Signature and Heuristics Bypass: API Encryption
API's can speak to the functionality of the malware, GetAsyncKeyState for example, is used by keyloggers primarily. With C++ this is prominent, take the following code snippet for example:
The function you see in the Gist above is a snippet taken from a custom red team trojan of mine; Disclaimer - All of my code is meant for legitimate security professional use, none of it is intended for malicious purposes, and anything that you do with any code is entirely your own responsibility - Notice the API UpdateRegistry with its arguments, is common for C++ code, and the code written in the languages that C++ provides this vital link to Windows API's and functions to. These would obviously be obfuscated, or be part of a false trail that does not produce anything vital to discovering the actual functionality and authors of the malware. All of your C++ RedTeamAgent API's are in the executable file in the import table, which is very visible to the malware analyst looking at the .exe file. All API's are made equal (in that there are no malicious API's, only the people using them), there are however API's that are commonly used in malware (represent key functionality), and are thus flagged by machine learning and AI tools especially easily, commonly included in this list are API's that will allow the program to communicate over the internet, for example:
- HttpOpenRequest, HttpSendRequest and other Wininet functions
- GetAsyncKeyState, and other API's and functions widely used by key-loggers
- DownloadUrlToFile
In combination with searching for important strings and decrypting them (to find URL's and domains, for example), an analyst can begin to understand how the program works. As an attacker, we should employ tactics and techniques to evade defenses and detection based on our understanding of how defenders and defensive and forensic investigative services and analysts work (these are the people we are testing as red team operators). We should;
- Encrypt API's that represent key functionality
- Dynamically load API's
Encrypt API's that represent key functionality in C++
RC4 encryption added to the RedTeamAgent as seen in the Gist below, there are accompanying RC4 header and .cpp files that are part of the project solution, these types of encryption algorithm open source projects are available on GitHub. They are relatively easy to implement in source code, as seen below.
The RC4 key that is used to encrypt the API (string) can be generated using CyberChef.
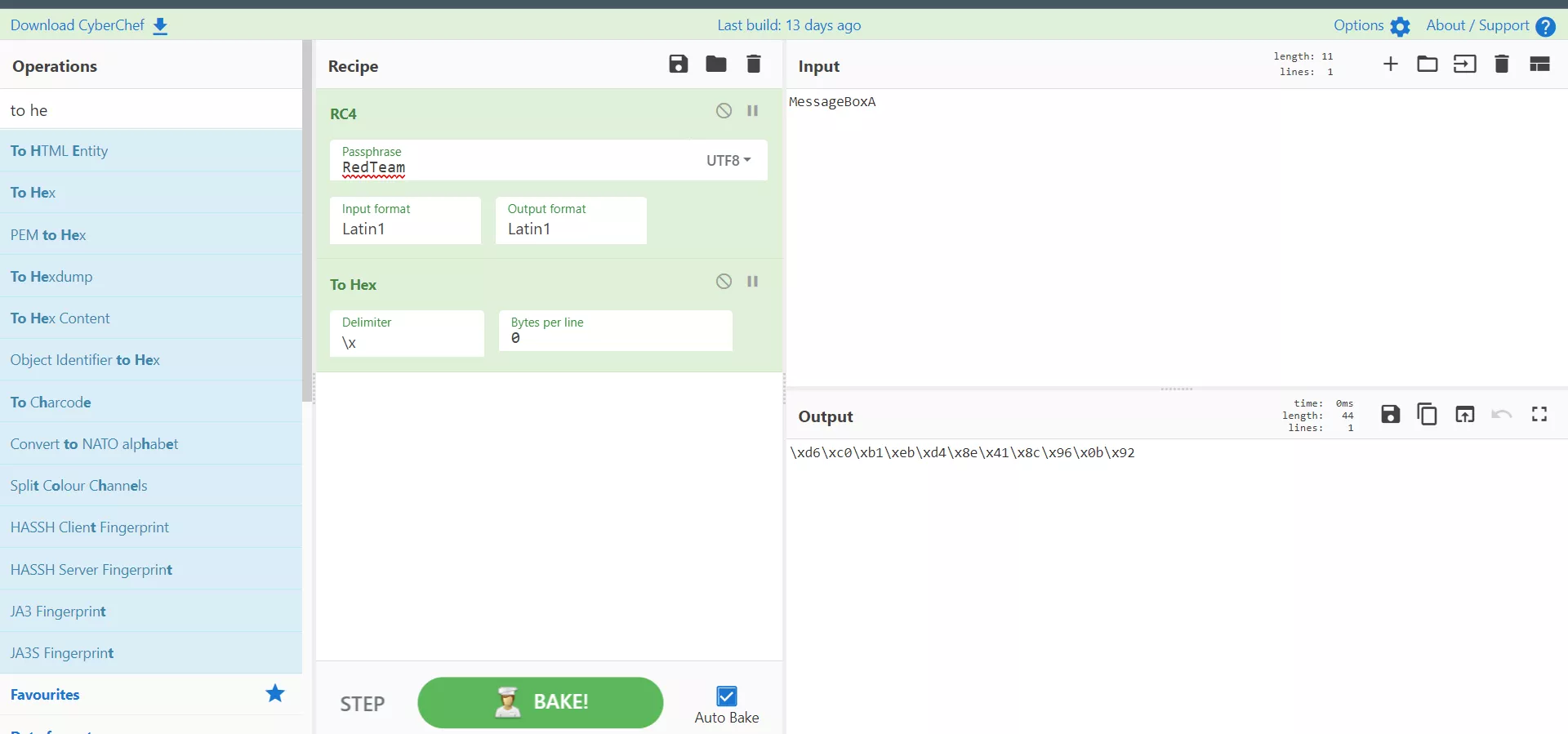
And the output below...

Message Box API in C++, using the useful structures feature in C++. The engineer could create a structure to get APIs, and group the values together.
And the output below...

Another example of the message box API without the structure for the APIs.
Blending in...Or: Making the program look as legitimate, and as harmless as possible...
In order to blend in (which is the preferred tactic for defense evasion), the following actions may be implemented/included in your C++ code. The analyst will have false positives to clear that will have to be emulated to remain undetected.
- Include legitimate APIs
- Registering a window
- Calling DirectX
- Opening GL
- Initialize sound libraries
- Include a legitimate application taken from GitHub.
Keep following me on social media to stay tuned for the follow up to this post...
Share this with your network
Grant Knoetze
IT Support Specialist Cybersecurity Analyst Software Developer